1. Kyverno policies provide a declarative way to secure Kubernetes clusters by enforcing rules for configuration, access, and resource management.
2. These policies help ensure compliance, enforce pod security standards, restrict namespace deletions, and more.
3. The traditional CLI approach to applying Kyverno policies works but is error-prone and lacks visibility.
4. Devtron offers a user-friendly GUI to apply and manage Kyverno policies, improving observability and ease of use.
Securing Kubernetes is a top priority for DevOps and platform engineering teams. Whether you’re adopting Kubernetes for the first time or scaling your production clusters, implementing Kyverno policies helps automate the enforcement of security best practices and reduce vulnerabilities.
In this blog, we’ll explore how to apply Kyverno policies: both via CLI and using the Devtron platform.
What are Kyverno Policies?
Kyverno is a policy engine designed specifically for Kubernetes. It allows you to define security, compliance, and operational policies in YAML and apply them directly to your Kubernetes clusters.
A Kyverno policy is a set of rules that validate, mutate, or generate resources. These policies enable you to:
- Restrict updates or deletions of critical resources
- Enforce naming conventions
- Set pod security controls
- Validate image registries
- Auto-label namespaces or workloads
Kyverno Policy Features
- Declarative management using YAML files
- Context-aware enforcement based on Kubernetes object state
- Dynamic policy updates as resources change
- Policy testing before enforcing rules
- CI/CD integration to shift security left
- Multi-cluster support
- Open-source and CNCF-hosted
These features make Kyverno policies highly adaptable to dynamic Kubernetes environments.
Why You Need Kyverno Policies
Enforcing security manually at scale in Kubernetes is risky. Here’s where Kyverno policies come into play:
- Resource validation: Automatically validate manifests to prevent misconfigurations.
- Access control: Restrict who can edit or delete specific resources.
- Pod security enforcement: Ensure containers don’t run as root or use disallowed capabilities.
- Namespace protection: Prevent accidental deletion of critical namespaces like
kube-system. - Regulatory compliance: Enforce the presence of specific labels or annotations.
Why Prevent Namespace Deletion Using Kyverno
Certain namespaces in Kubernetes are foundational:
default: For user workloadskube-system: Houses core services like kube-dns, kube-proxykube-public: Readable by unauthenticated userskube-node-lease: Maintains node health via heartbeats
Deleting any of these can lead to:
- Loss of critical workloads
- Security gaps
- Compliance issues
- Billing inaccuracies in multi-team setups
Kyverno can block deletions with a simple policy.
Traditional Command-line Approach to Applying Kyverno Policies
Step 1: Install Kyverno CRDs
kubectl create -f <https://github.com/kyverno/kyverno/releases/download/v1.8.5/install.yaml>Step 2: Create a YAML file named prevent-deletion.yaml
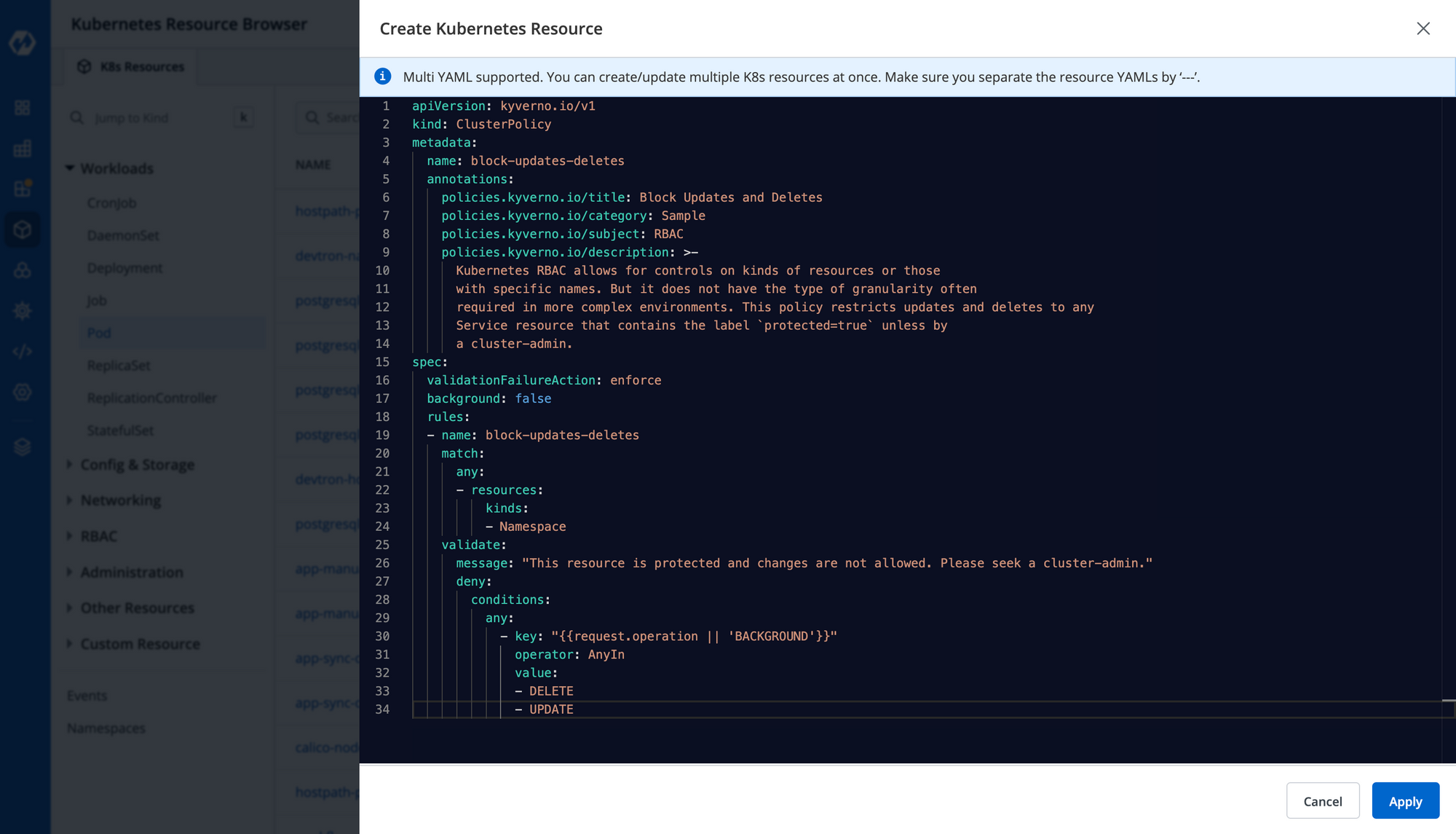
apiVersion: kyverno.io/v1
kind: ClusterPolicy
metadata:
name: block-updates-deletes
annotations:
policies.kyverno.io/title: Block Updates and Deletes
policies.kyverno.io/category: Sample
policies.kyverno.io/subject: RBAC
policies.kyverno.io/description: >-
Kubernetes RBAC allows for controls on kinds of resources or those
with specific names. But it does not have the type of granularity often required in more complex environments. This policy restricts updates and deletes to any Service resource that contains the label `protected=true` unless by a cluster-admin.
spec:
validationFailureAction: enforce
background: false
rules:
- name: block-updates-deletes
match:
any:
- resources:
kinds:
- Namespace
validate:
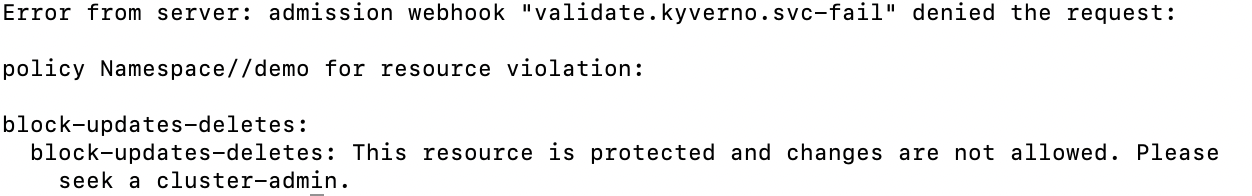
message: "This resource is protected and changes are not allowed. Please seek a cluster-admin."
deny:
conditions:
any:
- key: "{{request.operation || 'BACKGROUND'}}"
operator: AnyIn
value:
- DELETE
- UPDATE
Step 3: Apply the above-created manifest
kubectl apply -f prevent-deletion.yaml
Step 4: Create a namespace named `demo` to test the policy
kubectl create ns demokubectl delete ns demo
CLI Limitations
- Prone to typos and errors
- Low observability of applied policies
- Repetitive troubleshooting
- Hard to scale across teams and clusters
Adding Kyverno policies through Devtron
Devtron provides a web-based GUI interface to easily view, edit, and debug your policies across clusters and resources. Resource browser in Devtron allows you to view configurations side by side for comparison, and managing multiple security policies is a breeze. Let us see how you can set up policies using the Devtron Platform.
If you haven’t installed Devtron yet, feel free to install it from the documentation.
Step 1: Install CRDs
You can install CRDs via Helm or kubectl directly from Devtron's built-in terminal.
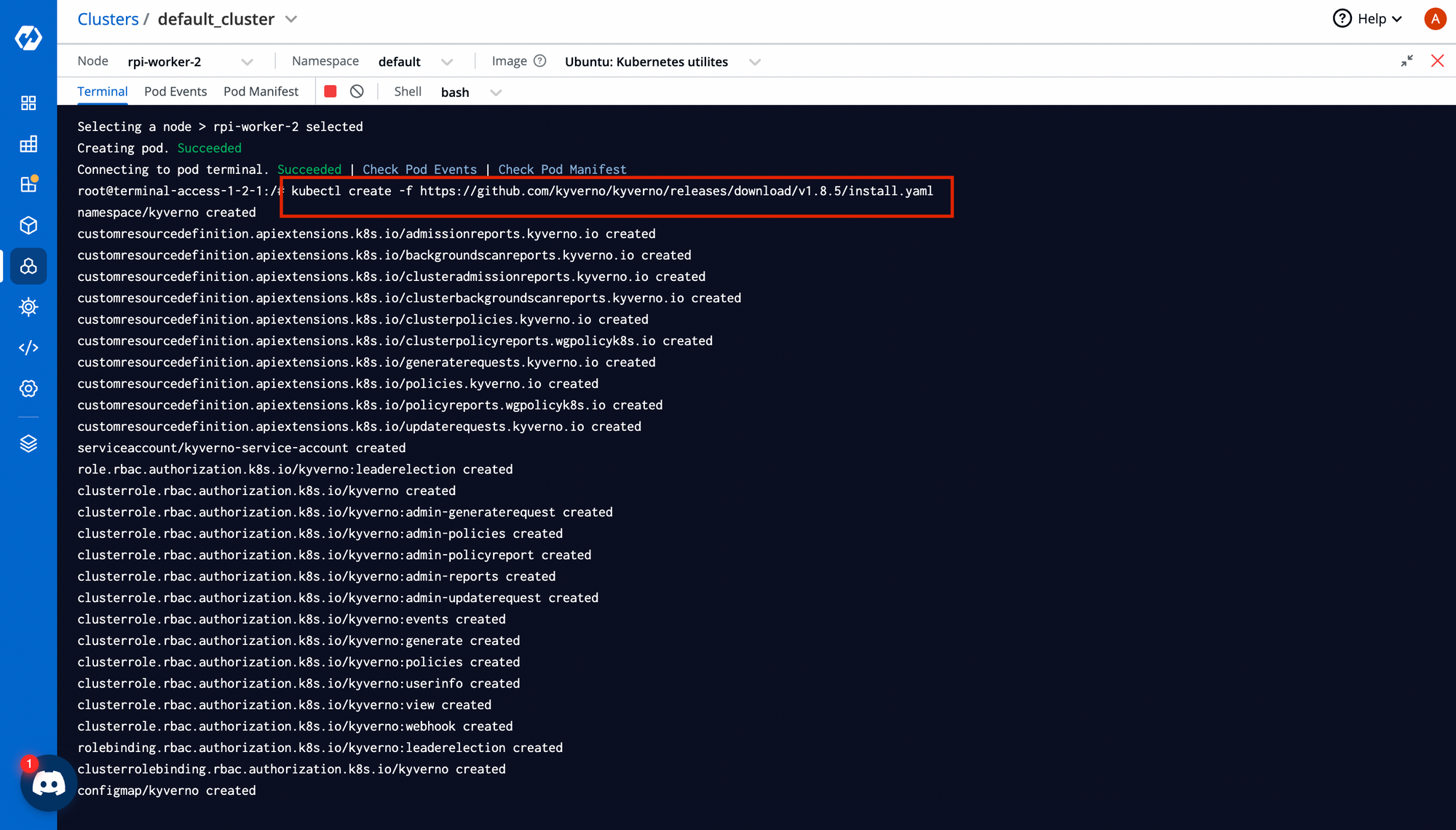
Navigate to:Clusters → Select Cluster → Terminal
Paste your CRD install command:
kubectl create -f https://github.com/kyverno/kyverno/releases/download/v1.8.5/install.yaml
Step 2: Use Resource Browser
Go to Resource Browser → Create Resource, and paste your Kyverno policy YAML. Click Apply.
This visual approach provides:
- Easier debugging
- Side-by-side config comparison
- Faster multi-cluster policy deployment
Paste your Kyverno policy and click on Apply.
Once the manifest has been deployed, you can view your policy in the Custom Resource section, as shown below.
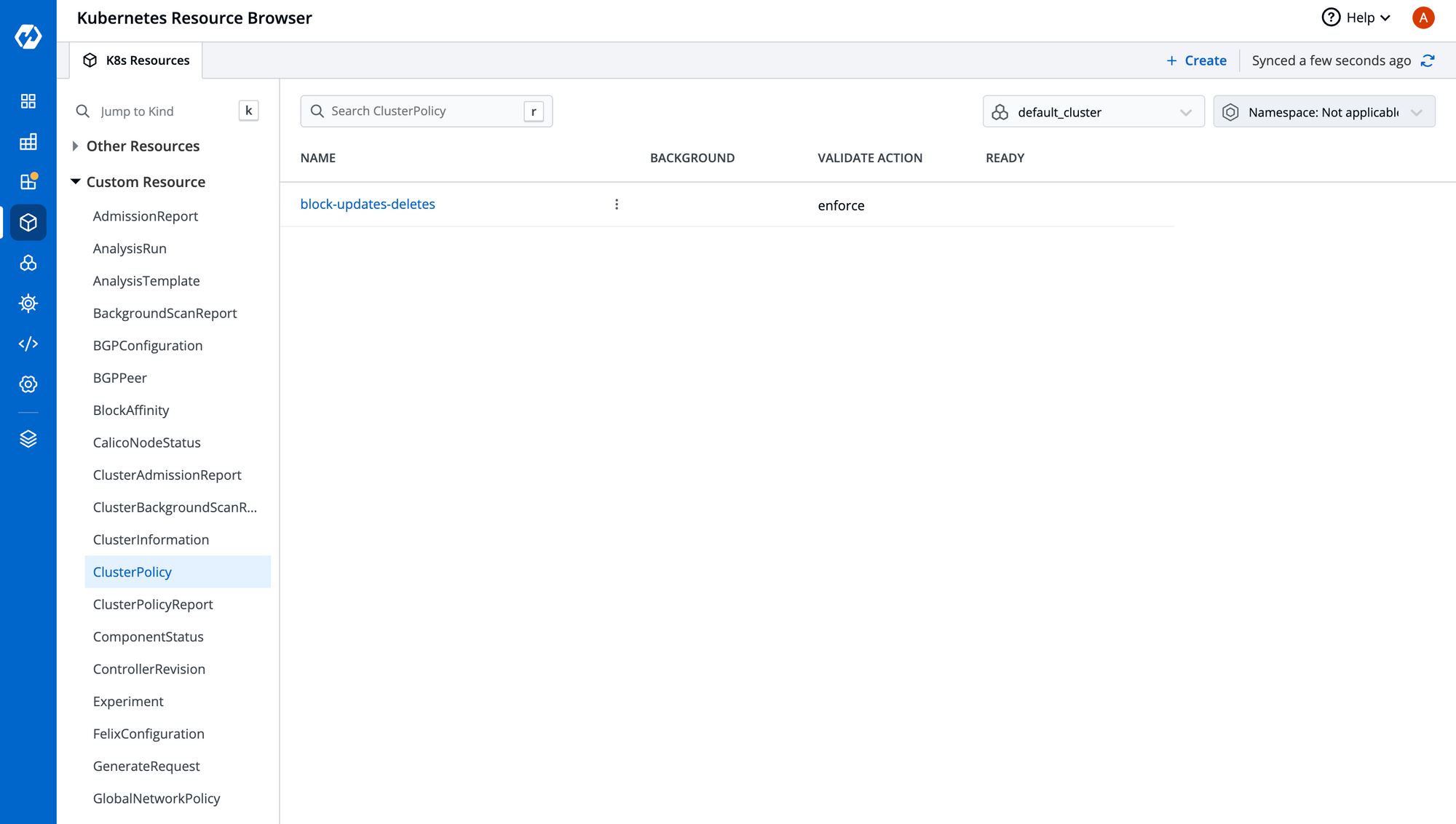
Step 3: Validate Your Policy
Use the in-browser terminal to run:
kubectl get ns
kubectl delete ns <namespace-name>
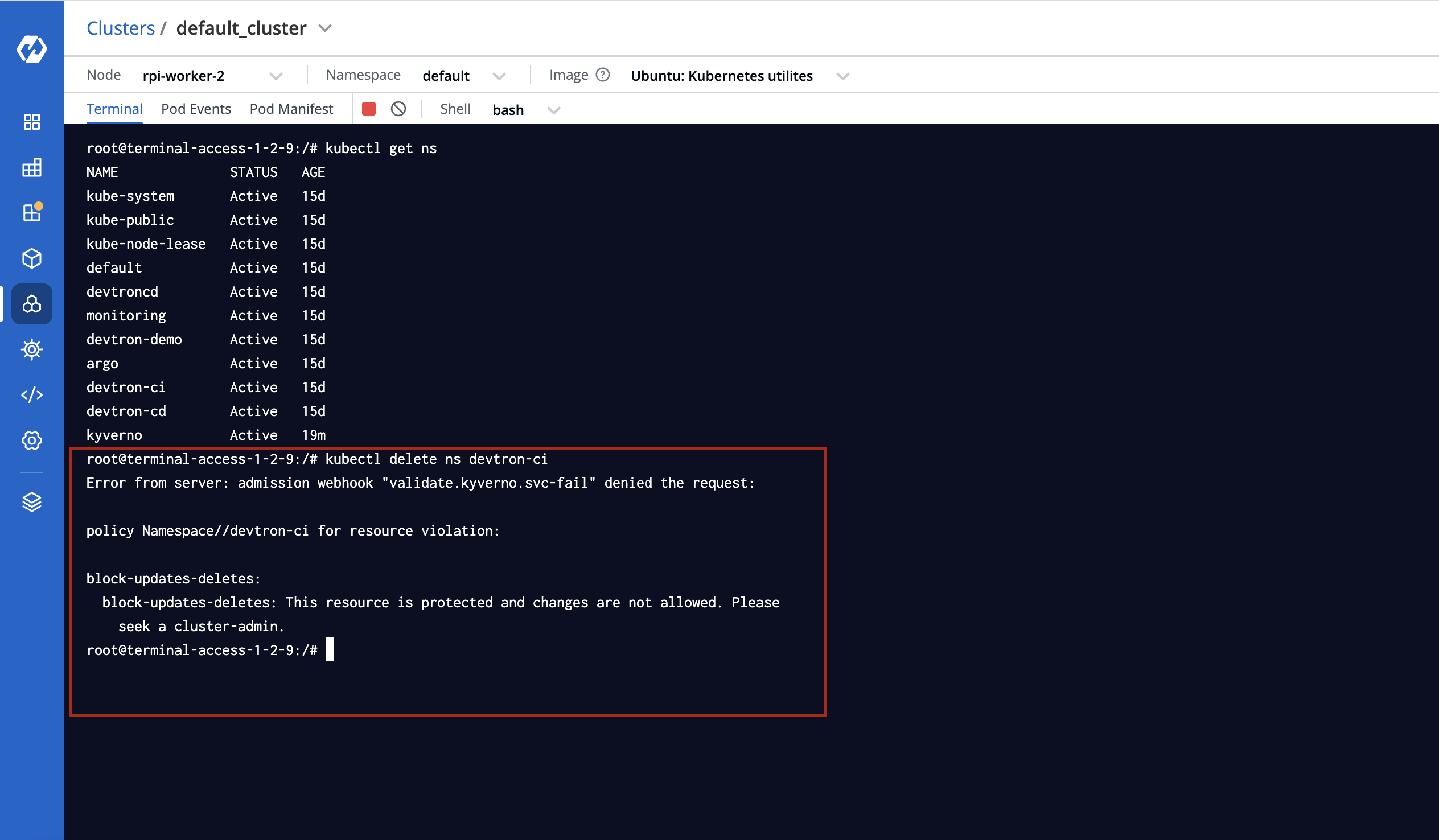
The policy should block deletion attempts if correctly configured.
Hurray!! We have successfully implemented the Kyverno policies to restrict the deletion of namespaces using Devtron.
Benefits of Using Devtron for Kyverno Policy Management
- GUI for easy management and observability
- Resource-level diffs and audit trails
- No manual kubectl errors
- Devtron CLI support for advanced automation
👉 Schedule a demo to see how Devtron simplifies Kubernetes policy management.
Conclusion
In a world where Kubernetes misconfigurations are one of the leading causes of downtime and security breaches, Kyverno policies are essential for preventive security.
- Secure your clusters
- Prevent unauthorized changes
- Enforce governance at scale
If you already use Devtron, make sure to integrate Kyverno today. And get ready for Devtron’s agentic AI, which will redefine how platform teams manage policy automation in Kubernetes.
FAQ
What are Kyverno Policies in Kubernetes?
Kyverno Policies are a set of declarative rules used to validate, mutate, or generate Kubernetes resources. They help enforce best practices, security controls, and compliance in Kubernetes environments.
Why should I use Kyverno instead of OPA Gatekeeper?
Kyverno is Kubernetes-native and uses familiar YAML syntax, making it easier for cluster administrators and developers. It integrates seamlessly into CI/CD workflows and requires less learning curve compared to Rego-based OPA policies.
Can Kyverno block namespace deletion in Kubernetes?
Yes, Kyverno can block the deletion of specific namespaces like kube-system, default, or any custom namespace by applying a validation rule using a ClusterPolicy.
How do I apply Kyverno policies using Devtron?
Devtron allows you to apply Kyverno policies through its GUI-based Resource Browser. You can paste your policy YAML, apply it, and monitor its enforcement visually, no CLI required.
Is Kyverno suitable for multi-cluster environments?
Yes, Kyverno supports multi-cluster policy management, allowing you to apply and enforce consistent policies across all your Kubernetes environments.





