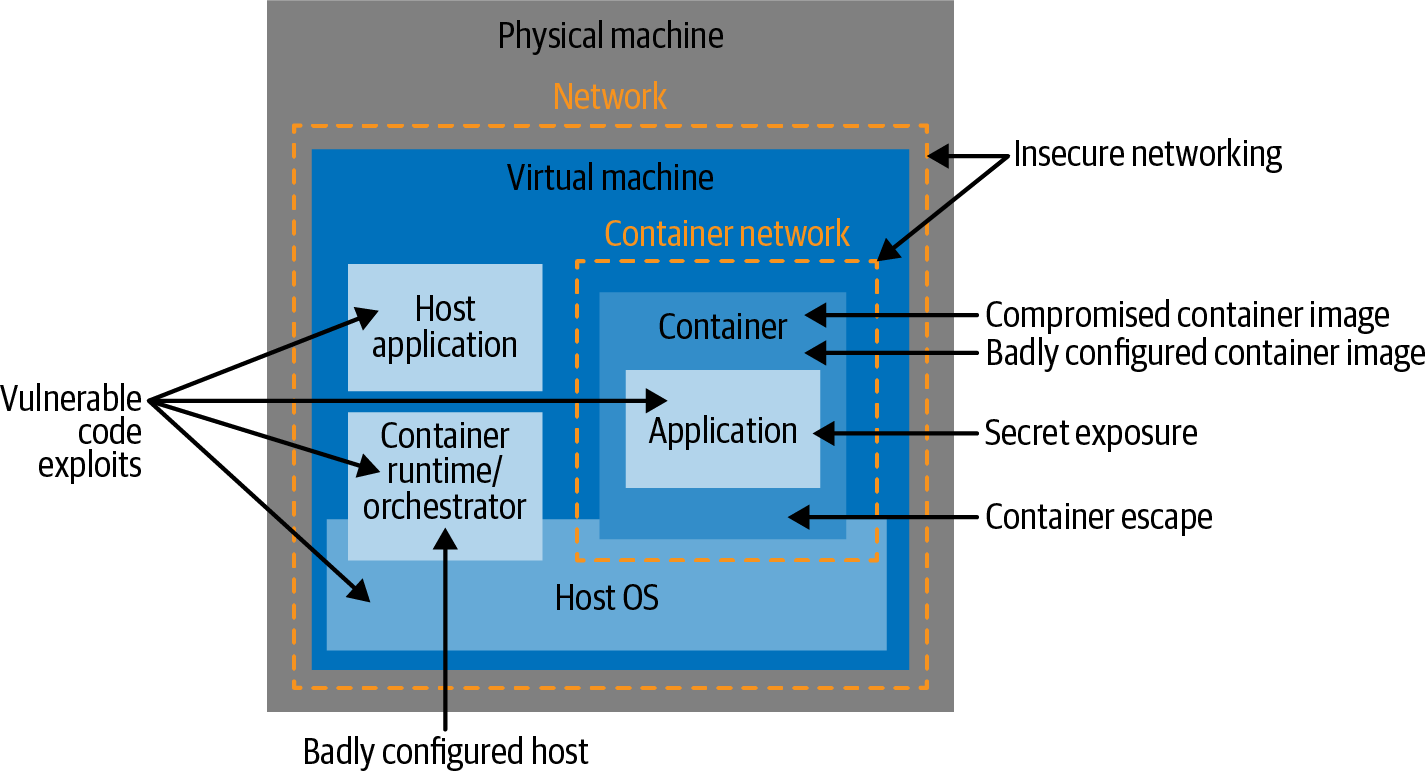
When it comes to cloud native ecosystem, containers are one of the most fundamental things, and it’s one of the most important part of the whole equation. In recent years, we have seen attackers attacking the supply chain space to exploit the vulnerabilities. Some famous examples include SolarWinds attack.
Here is a pictorial representation of some potential container security threats revolving around the ecosystem:
Even in 2022 the trend continues. Some major innovations in this space is done by a collaboration of many companies including Google, VMware, Chainguard and others.
In this blog, we will talk about the cosign project, which is a part of Sigstore. We will look how we can automate the signing of our images using Devtron.
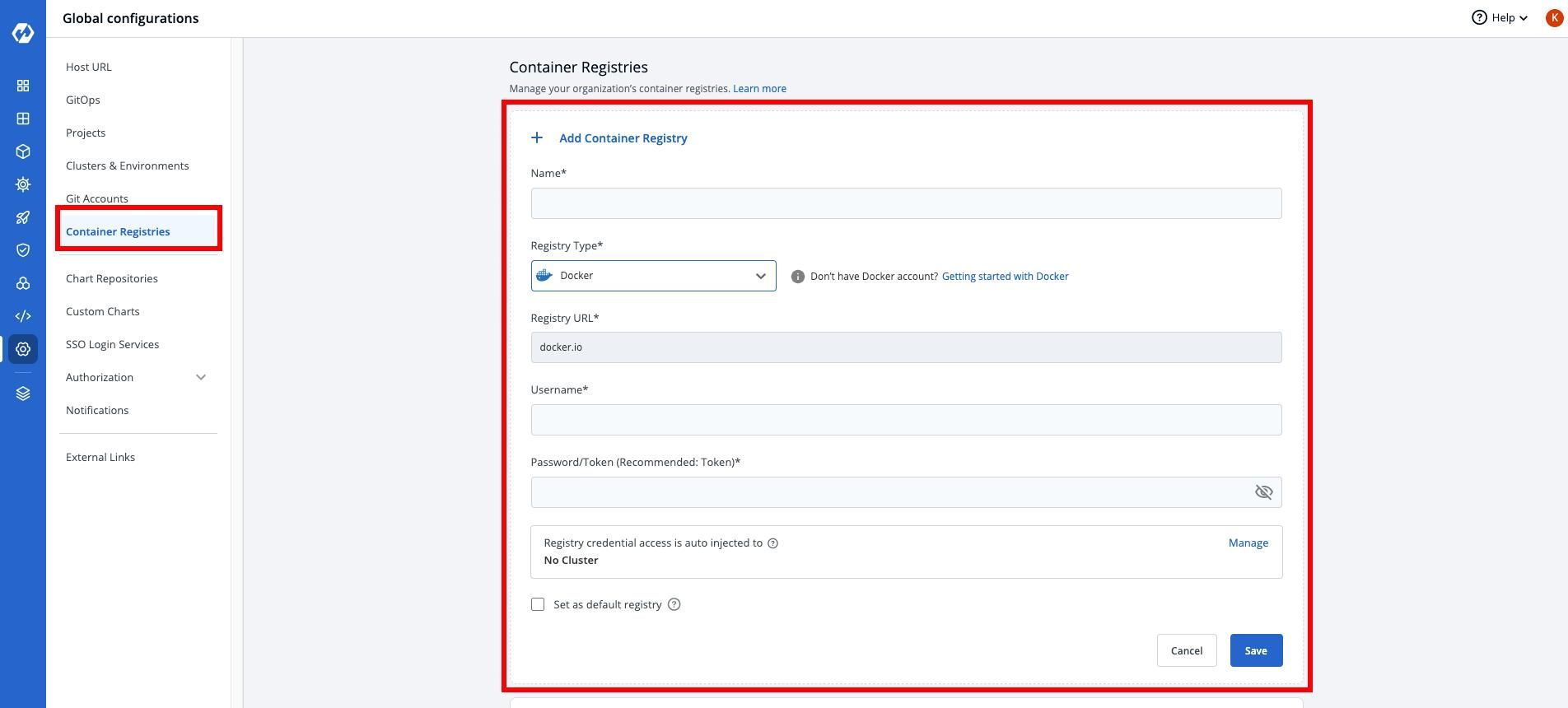
Set the global configurations
Make sure that the global configurations are set correctly, and you’ve attached your container registry to Devtron.
After this step, you need to go to application section and create an application. In this tutorial I’m choosing a custom application but if you want you can choose according to your choice.
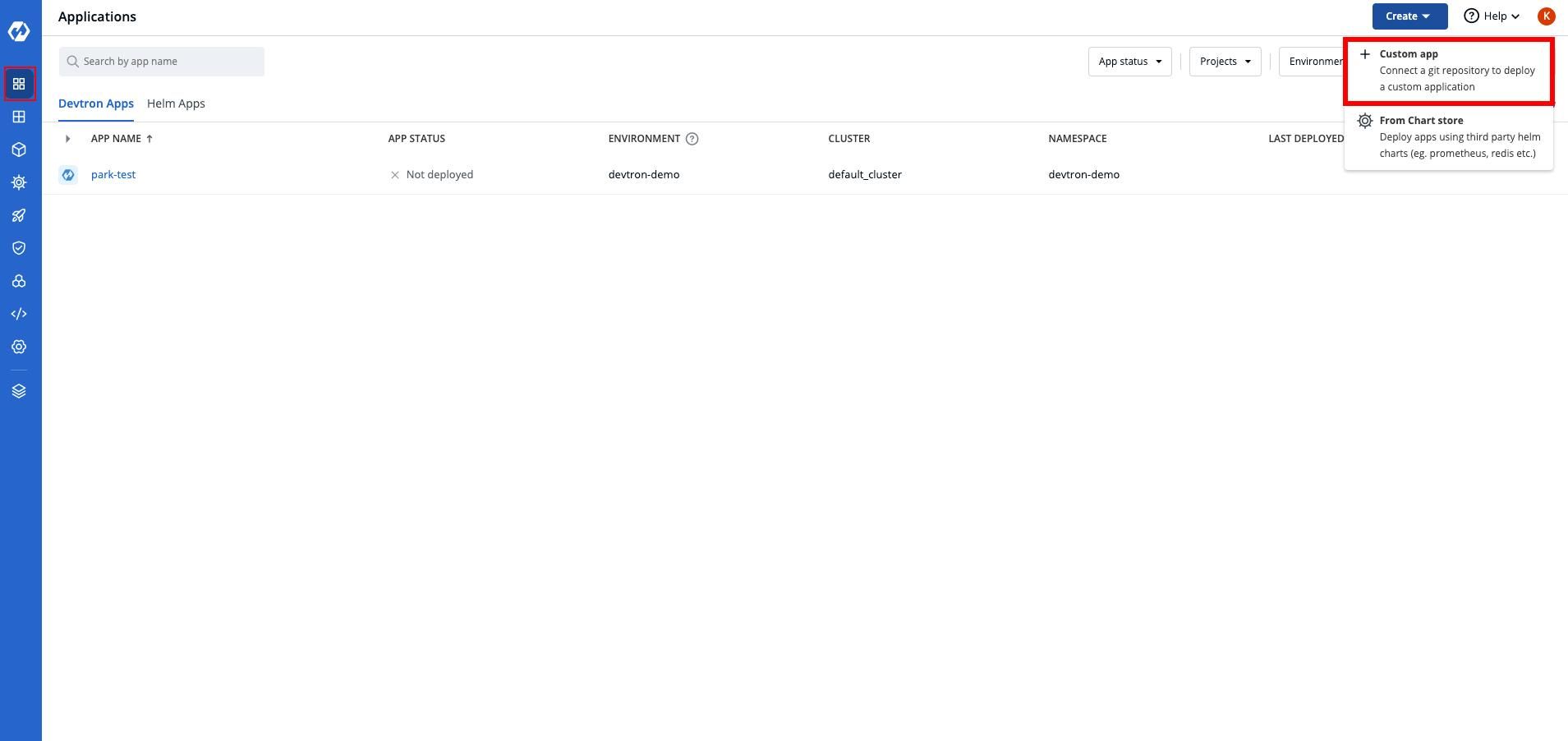
After this, give a name to your application and select the project you want to.
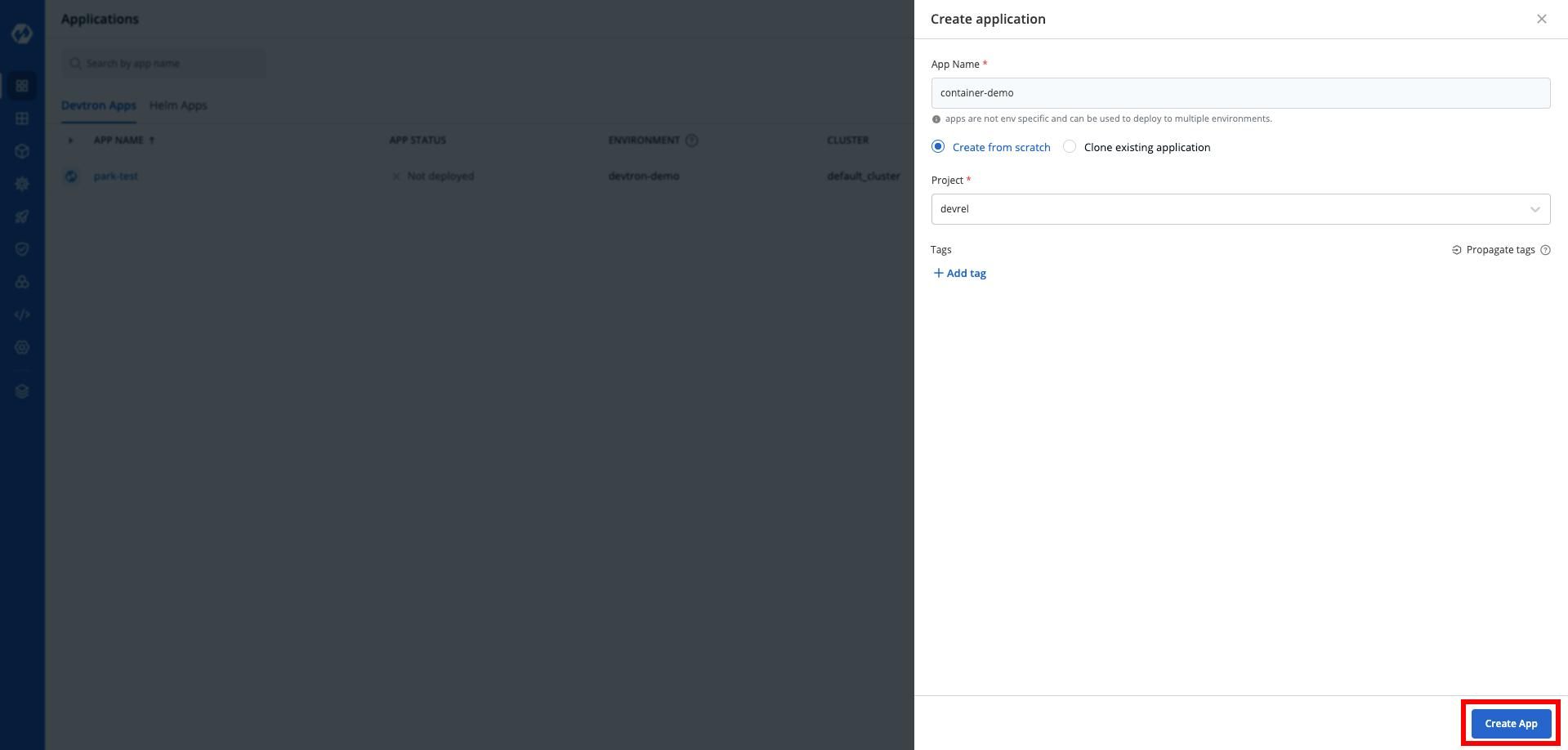
Now, after this, you need to complete the application specific settings in order to move ahead.
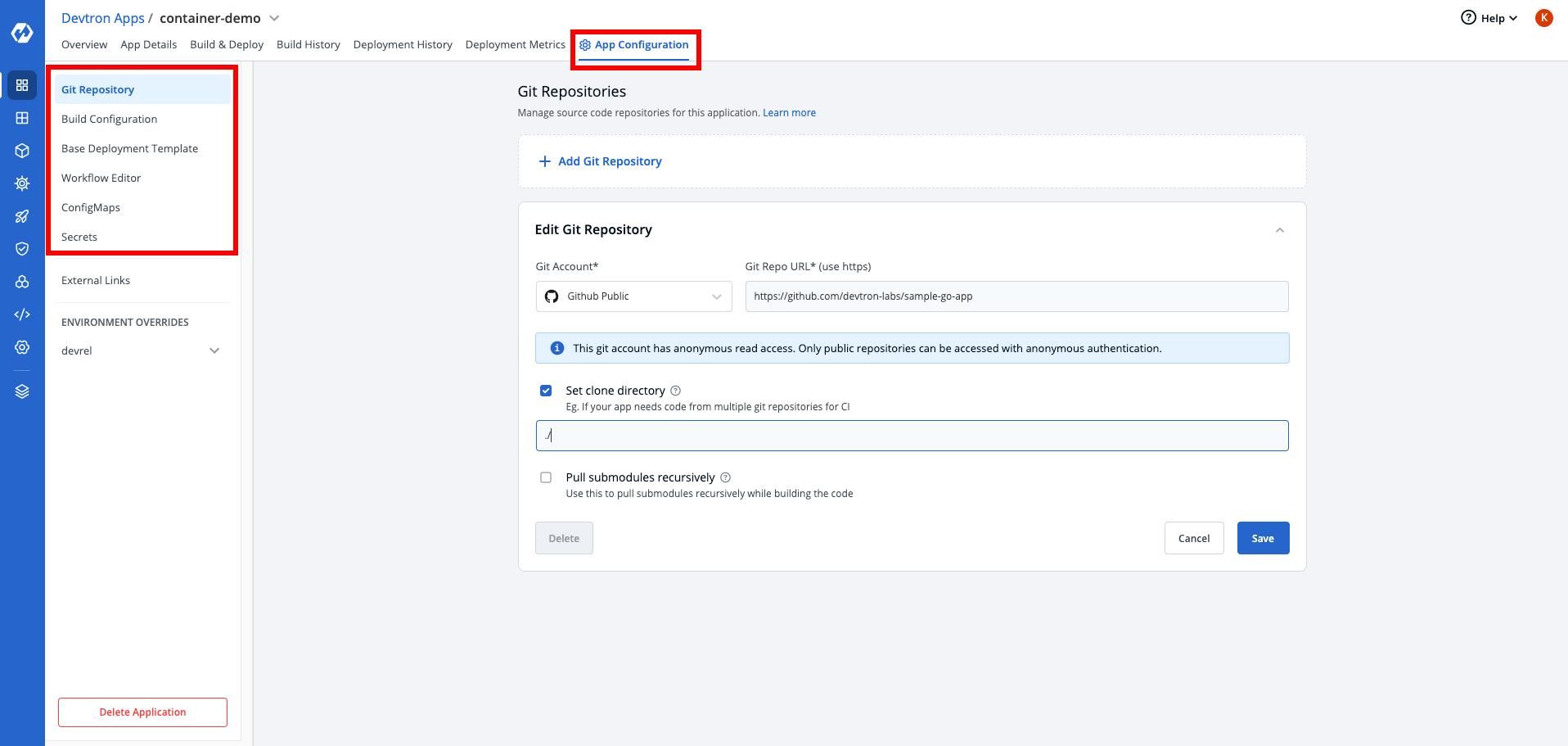
For the reference, you can try this sample go application by Devtron team.
Now, let’s setup continuous integration for our application. After setting this up, the container image will be built and that will be pushed to DockerHub.
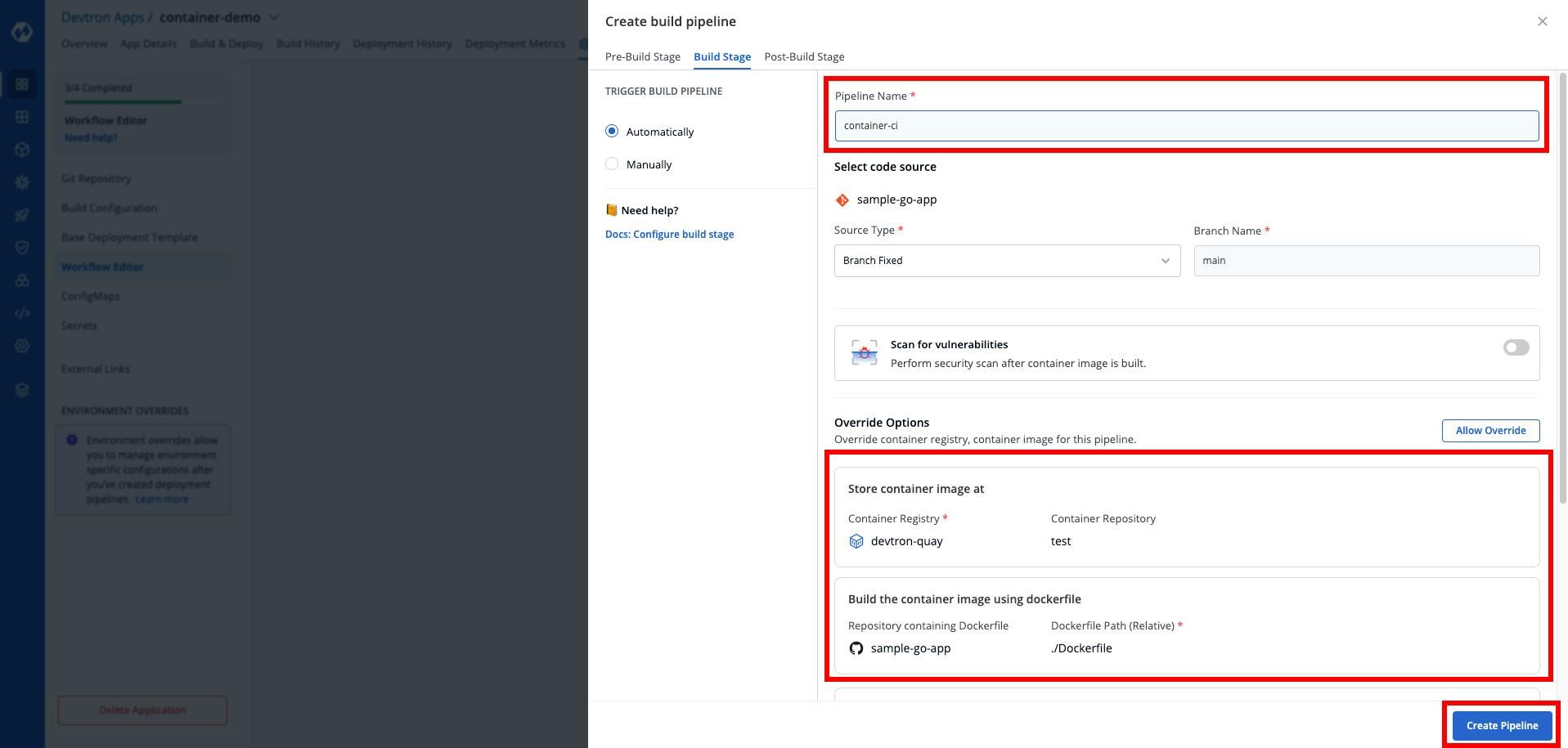
After setting up the continuous integration, we will use the following image post-build task to sign our image. Go to the post build stage and select custom script.
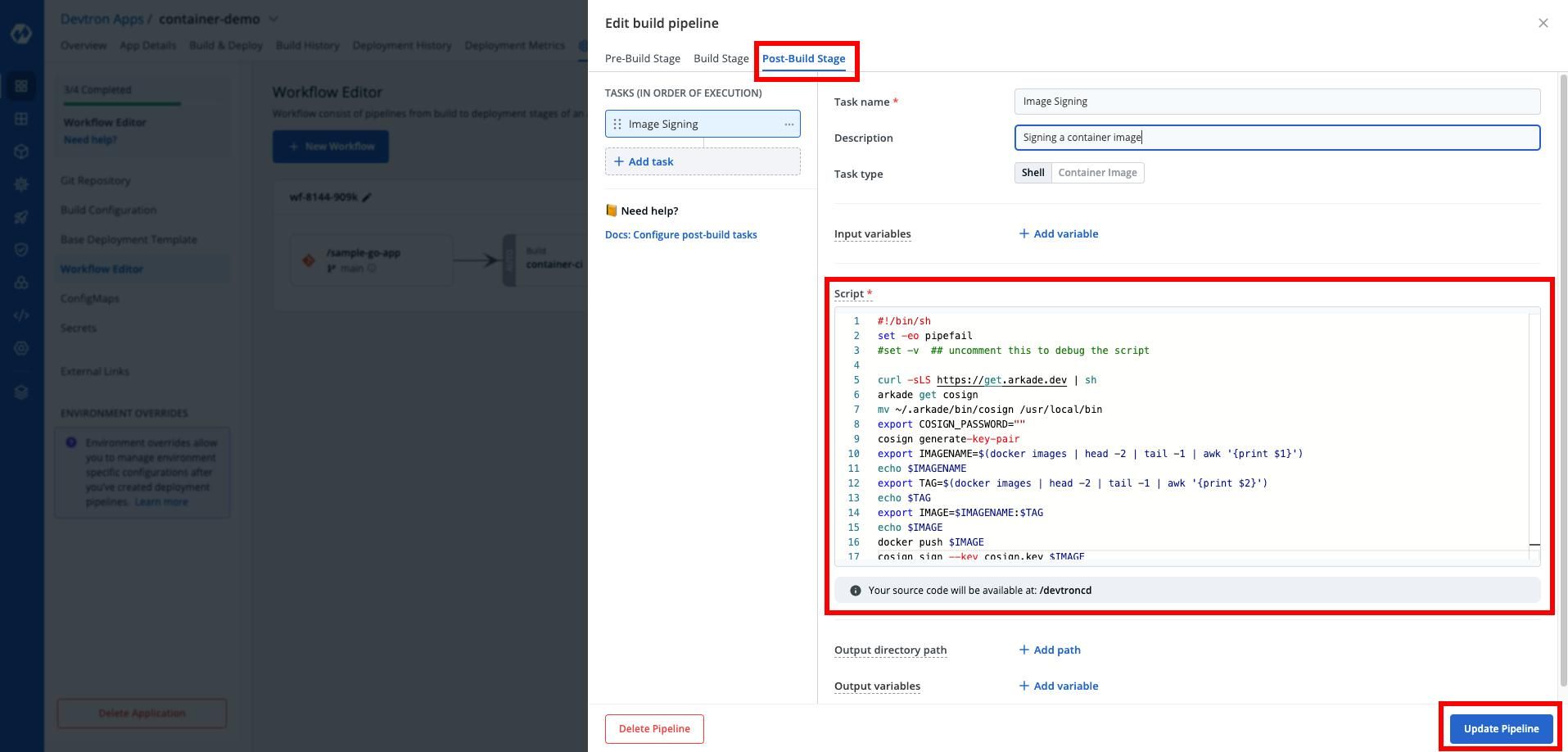
We need to write a custom script which will install cosign and sign the container image that we have built during the CI step.
I will use the custom script below to sign the container image that we have built.
#!/bin/sh
set -eo pipefail
#set -v ## uncomment this to debug the script
curl -sLS https://get.arkade.dev | sh
arkade get cosign
mv ~/.arkade/bin/cosign /usr/local/bin
export COSIGN_PASSWORD=""
cosign generate-key-pair
export IMAGENAME=$(docker images | head -2 | tail -1 | awk '{print $1}')
echo $IMAGENAME
export TAG=$(docker images | head -2 | tail -1 | awk '{print $2}')
echo $TAG
export IMAGE=$IMAGENAME:$TAG
echo $IMAGE
docker push $IMAGE
cosign sign --key cosign.key $IMAGE
Update the pipeline and go to build and deploy section. Choose the latest commit and then start the build.
After few minutes, the build will be successful and looking the logs you will notice that the signature is pushed to your docker registry.
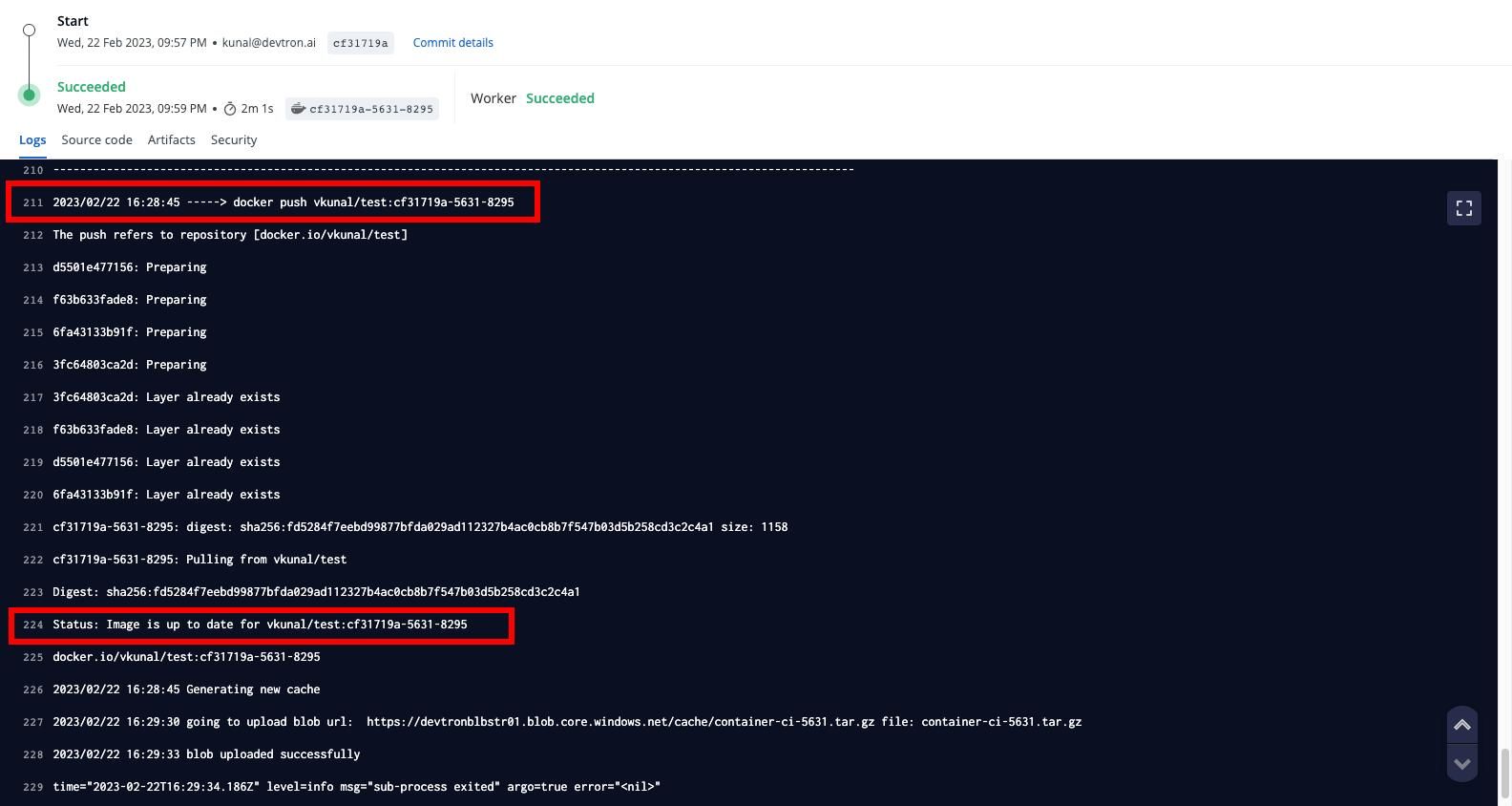
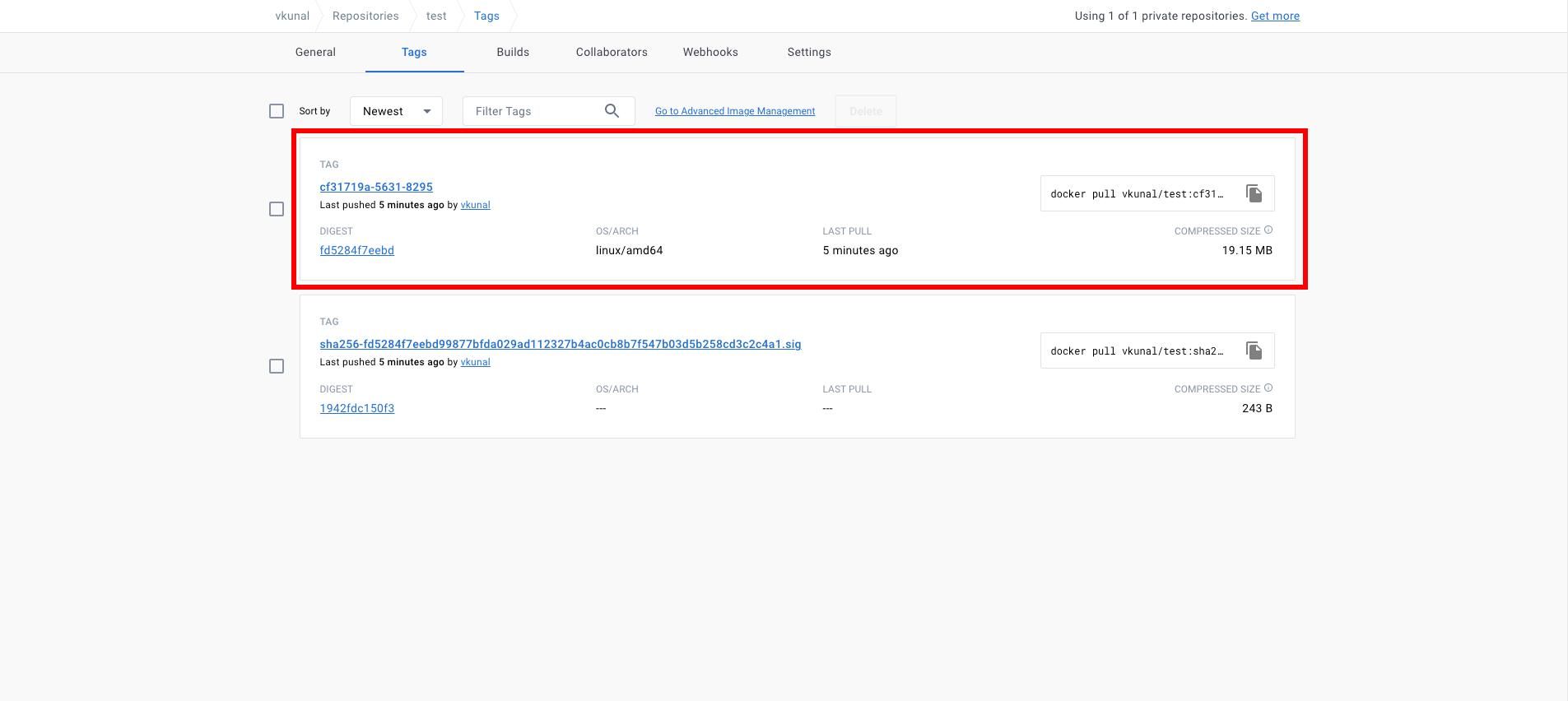
Now, If you will look at the docker registry, then you notice a signature being pushed to your registry.
You can also verify the same using the terminal, you can use the cosign triangulate command here.
cosign triangulate vkunal/test:cf31719a-5631-8295You will get your signature as the output, which basically shows that your image is signed.
You can learn more about Devtron here. Feel free to join our Discord community and share your experiences or doubts.
FAQ
What is Cosign and why is it important for container security?
Cosign is a Sigstore project that is used to sign and verify container images. It ensures the authenticity and integrity of your container images and helps prevent supply chain attacks such as image tampering or forgery.
How does image signing with Cosign work?
Image signing with Cosign works by generating a cryptographic key pair to sign Docker images. The signature is then attached to the container image in the registry, and users can verify the signature using Cosign’s verify or triangulate commands.
How can I automate container image signing in Devtron?
You can automate container image signing in Devtron by configuring a post-build custom script in the CI pipeline that installs and uses Cosign. This setup allows Docker images to be automatically signed after successful builds and ensures both the signed image and its signature are pushed to your container registry.
Why should I use Devtron for secure CI/CD pipelines?
Devtron seamlessly integrates with container registries and Cosign, simplifies the setup of secure, signed builds through an intuitive visual interface, and enables secure software supply chain practices without introducing additional tooling complexity.