1. RBAC (Role-Based Access Control) is a critical security strategy in Kubernetes, ensuring users have only the permissions they need.
2. SSO (Single Sign-On) simplifies authentication by integrating existing identity providers.
3. Manual access control is error-prone and can lead to vulnerable clusters, wasted time, and misconfigurations.
4. Devtron simplifies RBAC & SSO with a unified dashboard, fine-grained access control, and integrations with major providers.
5. Combining SSO + RBAC provides strong security, scalability, and centralized access management for Kubernetes.
Introduction
In the ever-evolving world of cloud-native computing, Kubernetes has emerged as a standard solution for container orchestration. However, managing access control across multiple Kubernetes clusters can quickly become a complex task, especially in large organizations with numerous teams and members. This is where the power of Devtron's Single Sign-On (SSO) and Role-Based Access Control (RBAC) comes into play, providing a secure and efficient solution for access management.
Authentication/Authorization
The very first way to secure something in the digital world is to set up authentication and authorization. The authentication can be handled by SSO, and the authorization can be done through RBAC for the Kubernetes environment.
Why RBAC Matters in Kubernetes
RBAC is a Kubernetes-native authorization mechanism that defines who can access what within your clusters. Without RBAC, organizations risk:
- Over-privileged access to sensitive resources
- Operational inefficiencies due to manual configuration
- Security risks such as unauthorized database deletions or production downtime
By adopting RBAC in Kubernetes, you ensure least-privilege access, one of the NIST Zero Trust security principles.
The Challenge of Manual Access Control
Imagine managing 50 Kubernetes clusters across multiple teams. Without proper SSO and RBAC, you face:
- Vulnerable clusters: Misconfigured or leaked kubeconfig files expose sensitive workloads.
- Kubeconfig distribution risks: Sharing static tokens or files increases the chance of breaches.
- Complex RBAC management: Manual configuration of ClusterRoles and RoleBindings is time-consuming, inconsistent, and error-prone.
This leads to wasted engineering hours, reduced agility, and potential compliance failures.
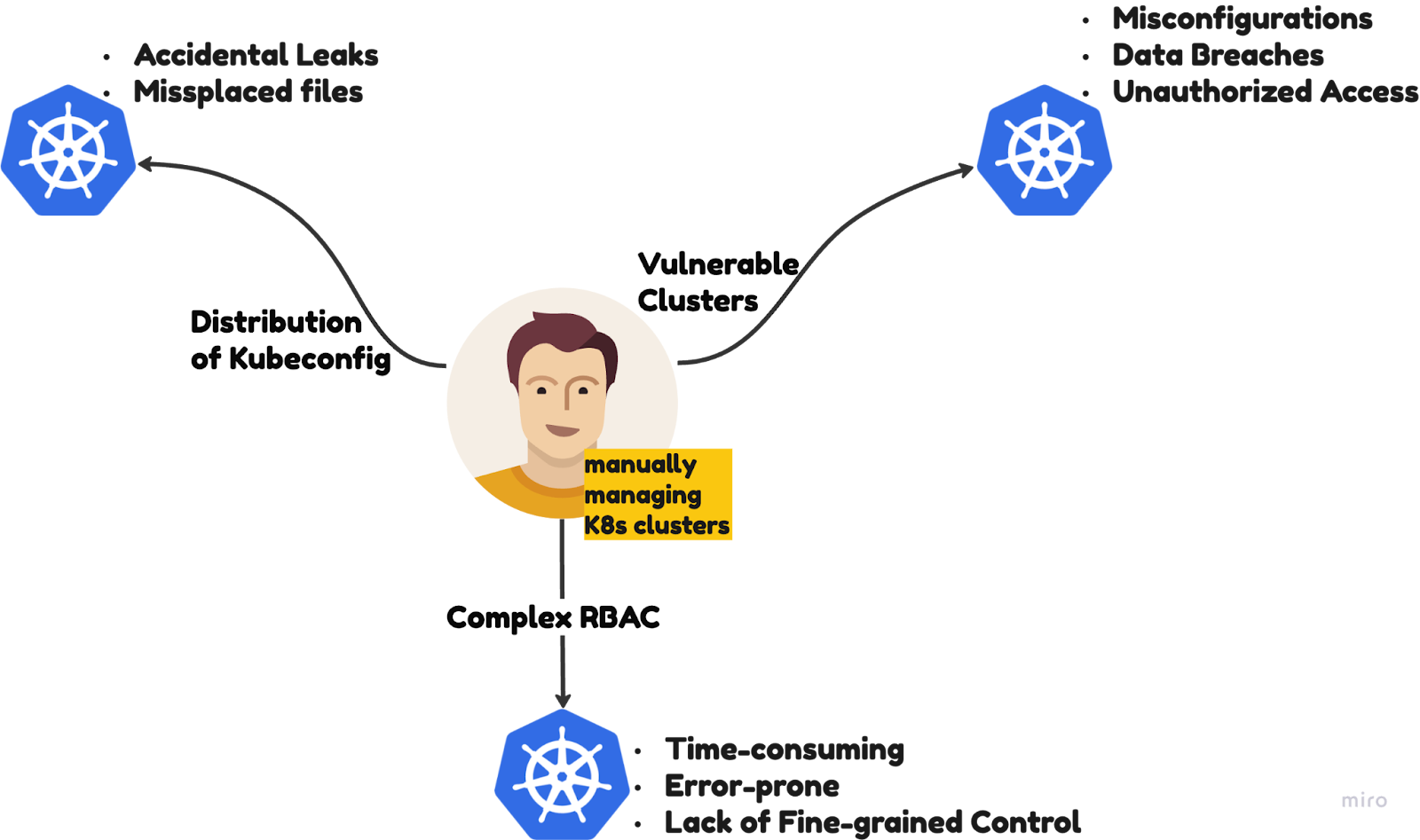
These are some major challenges that you may face when you choose to manage multiple clusters manually. And definitely, you don't want to spend time navigating through these complexities rather than focusing on what truly matters: efficient deployments and innovation.
Single Sign-On (SSO) for Kubernetes Authentication
Authentication is the first step in securing Kubernetes. With SSO, users log in once with their identity provider and gain access to authorized clusters. This removes the need to manage kubeconfig files and static tokens.
Benefits of SSO in Kubernetes:
- Centralized login with providers like Google, GitHub, GitLab, Microsoft, LDAP, OIDC, and OpenShift
- Seamless integration with IAM tools like Okta and Keycloak
- Reduced attack surface by eliminating static kubeconfig distribution
RBAC in Kubernetes: Fine-Grained Authorization
Once users are authenticated, RBAC handles authorization — defining what actions they can perform.
RBAC Components in Kubernetes:
- Roles & ClusterRoles: Define permissions at the namespace or cluster level
- RoleBindings & ClusterRoleBindings: Assign those permissions to users or groups
Challenges with Manual RBAC:
- Error-proneness in configuring roles at scale
- Scalability issues when new members join frequently
- Security concerns due to over-permissioned users
How Devtron Simplifies RBAC

Devtron provides:
- A GUI for RBAC management (no YAML complexity)
- User Access Management with Active/Inactive/TTL user states
- Granular permissions for Kubernetes resources and environments
- Centralized dashboard to manage RBAC across clusters
This ensures security, compliance, and operational efficiency.
Configure SSO with Google, GitHub, GitLab, Microsoft, LDAP, OIDC, and OpenShift. You can also integrate other identity and access management tools like Okta and Keycloak for managing user permissions.
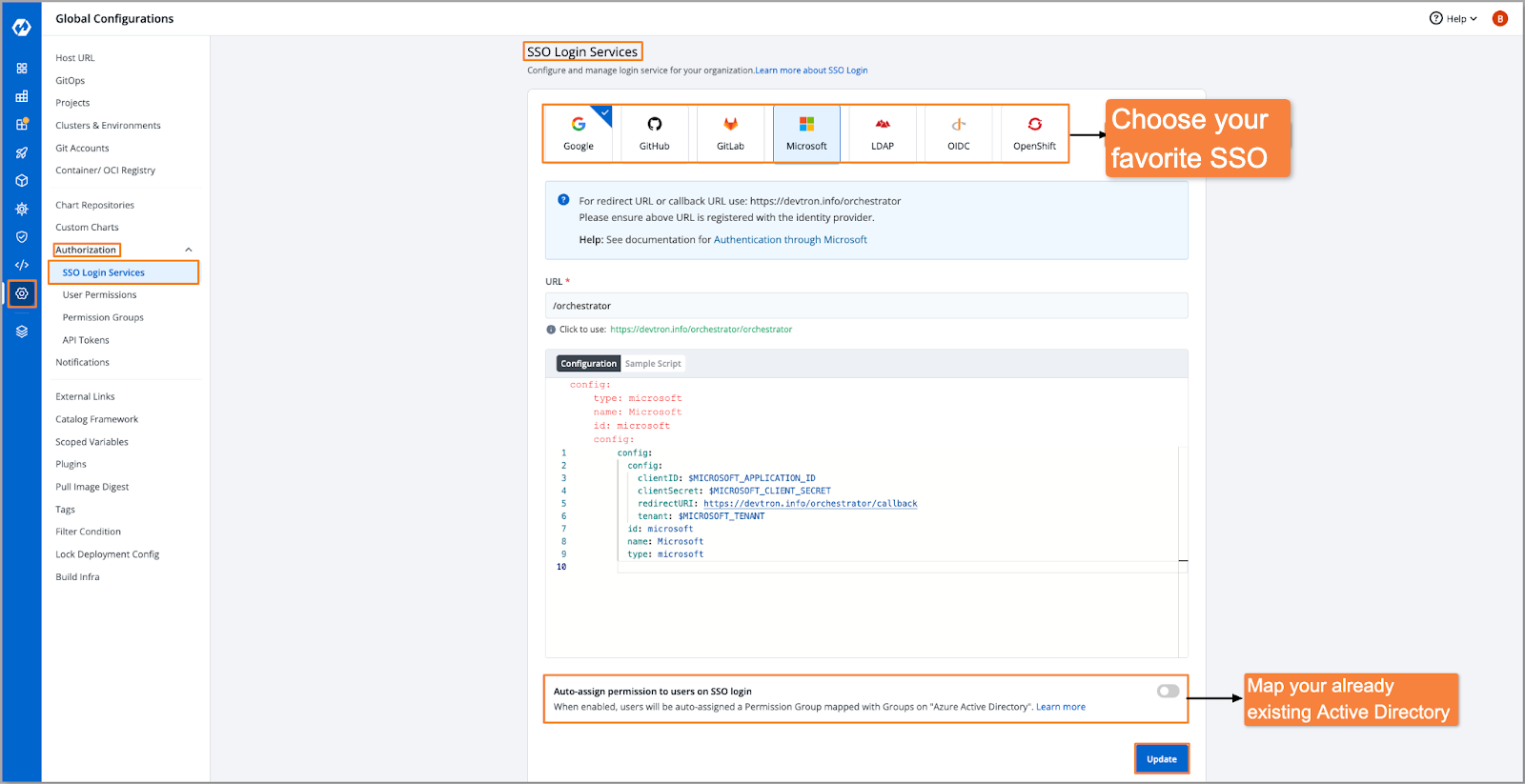
Fine-Grained Access Control with RBAC - Authorization
While SSO solves the authentication challenge for you. RBAC addresses the authorization aspect by allowing you to define granular permissions and restricting access to cluster resources for users. In Kubernetes, you can define roles, cluster roles, role bindings, and cluster role bindings to control access at both the namespace and cluster levels. While setting the manual configuration, you can face issues like:
- Error-Proneness and Complexities: Configuring a vast number of roles and permissions in Kubernetes makes it difficult to configure them all accurately. You can face the issue of inconsistent configuration.
- Scalability: To allow a new team member to access your cluster, you need to configure the RBAC again. Imagine doing this for each new member and every new cluster. Manually configuring RBAC results in inefficiency.
- Security Concerns: While configuring the RBAC manually, there are chances of granting more user access than is required. These will allow users to access sensitive resources like the production database. Now, think you mistakenly granted permission to users for databases, and users will fire a delete query on that.
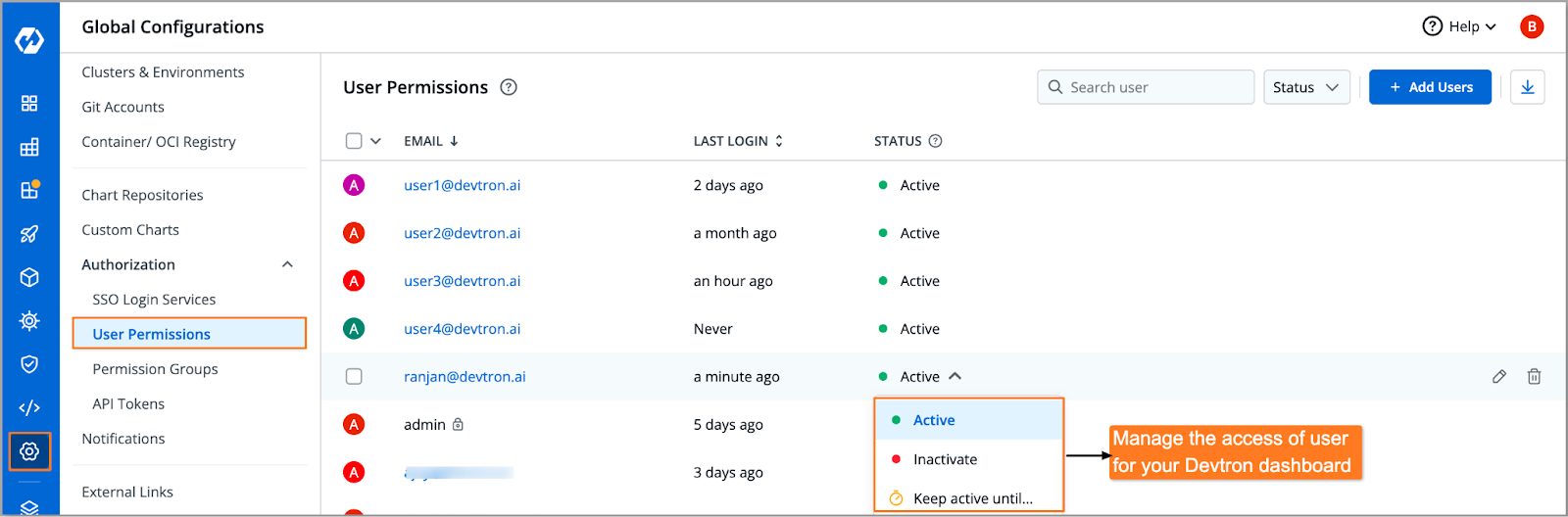
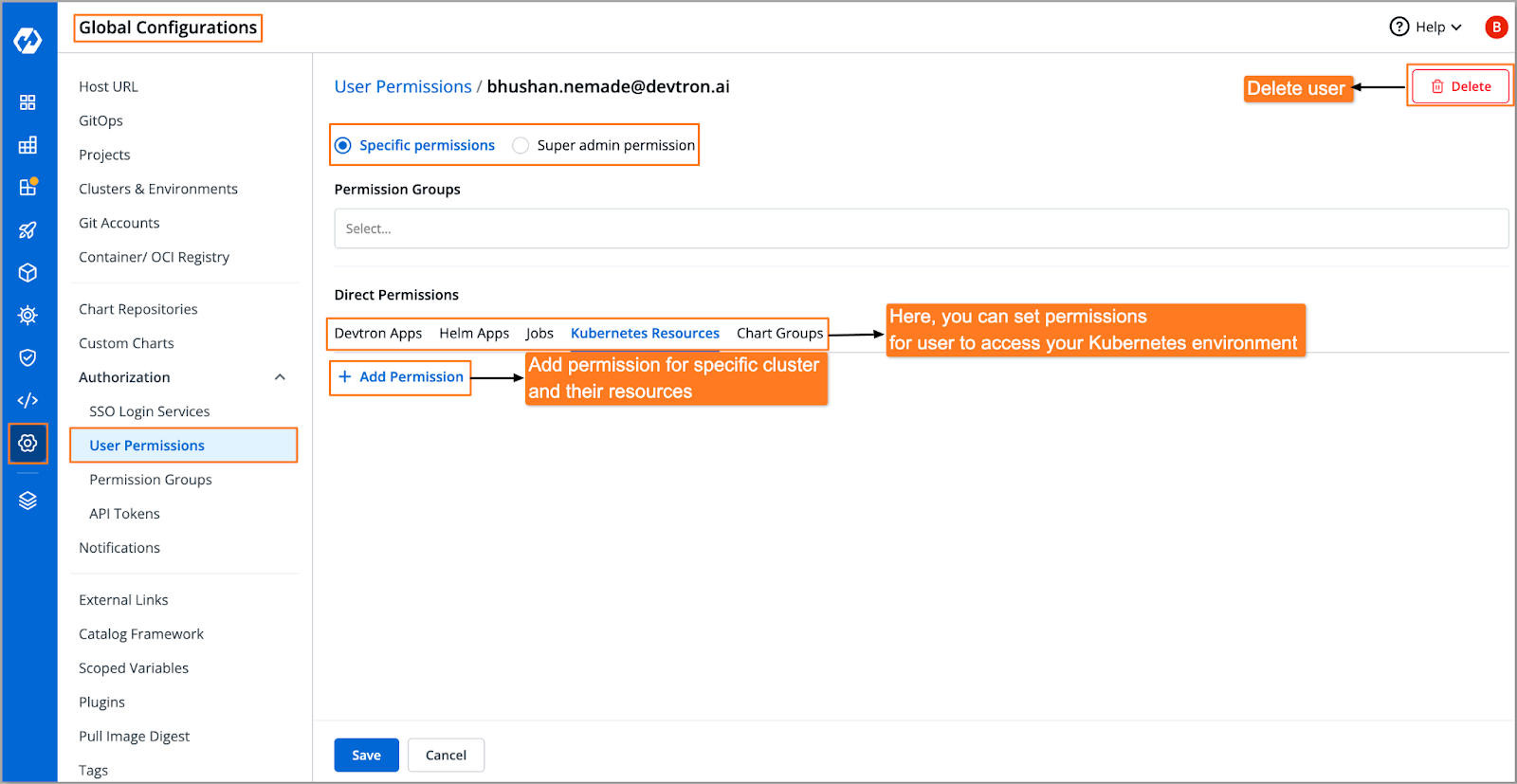
Devtron simplifies this process by providing a graphical user interface (GUI) for managing RBAC. RBAC in Devtron is specifically designed for the workflow of Kubernetes. It allows the administrator to manage access to Kubernetes clusters, environments, and all resources in the cluster. Ensures least-privileged access and creates a secure environment by defining roles and restricting access for other users. Devtron allows you to manage fine-grained access control down to the Kubernetes cluster resource level. You can grant users precise permissions for specific resources in the cluster. The User Access Management feature in Devtron allows you to add other users, like support engineers, and manage their access on your Devtron dashboard. You can mark the status of users as ‘Active’, ‘Inactive’, or ‘Keep active until’ (TTL). This feature gives you control over how other qualified users access your Devtron dashboard.
SSO + RBAC: The Secure Kubernetes Duo
When combined, SSO and RBAC provide a complete Kubernetes access strategy:
- Enhanced Security: Centralized authentication + least-privilege authorization
- Improved Manageability: Access managed centrally across multiple clusters
- Scalability & Flexibility: Seamless onboarding as teams and workloads grow
Devtron makes this combination effortless with one dashboard for both SSO and RBAC.
Devtron’s Advantage with RBAC & SSO
- Pre-built integrations with major SSO providers
- Easy-to-manage fine-grained RBAC controls
- Extended support for kubectl access with limited tokens
- Centralized, intuitive UI for secure Kubernetes access management
Conclusion
In modern cloud-native environments, RBAC in Kubernetes is not optional — it’s essential. Combined with SSO, it provides a secure, scalable, and efficient access strategy.
Devtron eliminates the complexity of managing SSO and RBAC by offering a unified dashboard, graphical management, and integrations with identity providers. This empowers organizations to secure Kubernetes clusters while enabling faster deployments. To learn more, check out this blog about control and secure kubectl access.
If you have any queries, don't hesitate to connect with us. Join the lively discussions and shared knowledge in our actively growing Discord Community.
FAQs
What is RBAC in Kubernetes?
RBAC (Role-Based Access Control) in Kubernetes is a security mechanism that defines which users or service accounts can perform specific actions on cluster resources.
Why is RBAC important for Kubernetes security?
RBAC enforces the principle of least privilege, ensuring users only have the permissions necessary for their tasks. This reduces the risk of unauthorized access or accidental changes in production.
How does SSO improve Kubernetes access management?
SSO (Single Sign-On) simplifies authentication by allowing users to log in with existing identity providers like Google, GitHub, or LDAP. This eliminates the need for kubeconfig sharing and enhances security.
Can RBAC and SSO be used together in Kubernetes?
Yes, RBAC and SSO complement each other. SSO handles authentication, while RBAC enforces authorization. Together, they create a secure and scalable access strategy for Kubernetes.
How does Devtron simplify RBAC and SSO management?
Devtron provides a centralized dashboard for configuring RBAC and SSO, integrates with popular identity providers, and offers a GUI for managing fine-grained permissions without writing YAML.






