The Kubernetes community has discovered a series of critical vulnerabilities affecting the widely used Ingress NGINX Controller, potentially exposing organizations to significant security risks. With over 40% of Kubernetes clusters utilizing this controller, understanding and mitigating these vulnerabilities is crucial for maintaining cluster security.
Understanding Ingress NGINX
Ingress NGINX is a popular Kubernetes ingress controller that translates Ingress objects into NGINX configurations, enabling secure and flexible network routing for containerized applications. It plays a critical role in exposing workload Pods to external networks while managing complex routing requirements.
Vulnerability Details
Technical Background
The vulnerabilities center around the Ingress NGINX admission controller, a component designed to validate incoming ingress objects before deployment. By default, these admission controllers are network-accessible without authentication, creating a significant attack vector.
Key Vulnerabilities
The discovered vulnerabilities (including CVE-2025-1098, CVE-2025-1974, CVE-2025-1097, CVE-2025-24514, and CVE-2025-24513) present multiple attack paths:
- Configuration Injection: Attackers can remotely inject malicious NGINX configurations through the admission controller.
- Remote Code Execution (RCE): Some vulnerabilities allow executing arbitrary code within the Ingress NGINX Controller's pod.
- Cluster-Wide Secret Exposure: Potential for accessing secrets across all namespaces, potentially leading to complete cluster takeover.
Severity Highlights
The most critical vulnerability, CVE-2025-1974, received a severe CVSS rating of 9.8. This vulnerability is particularly dangerous because:
- It can be exploited by any entity on the Pod network
- No administrative credentials are required
- Many network configurations might inadvertently expose the vulnerability
Mitigation
Temporary mitigation
Verify Your Installation Check if you're using Ingress NGINX:
kubectl get pods --all-namespaces --selector app.kubernetes.io/name=ingress-nginx
For Installations using Devtron
If you have deployed nginx using Devtron, navigate to Helm Apps and search for your nginx deployment name. Now, in the configure page, change the controller.admissionWebhooks.enabled to false.
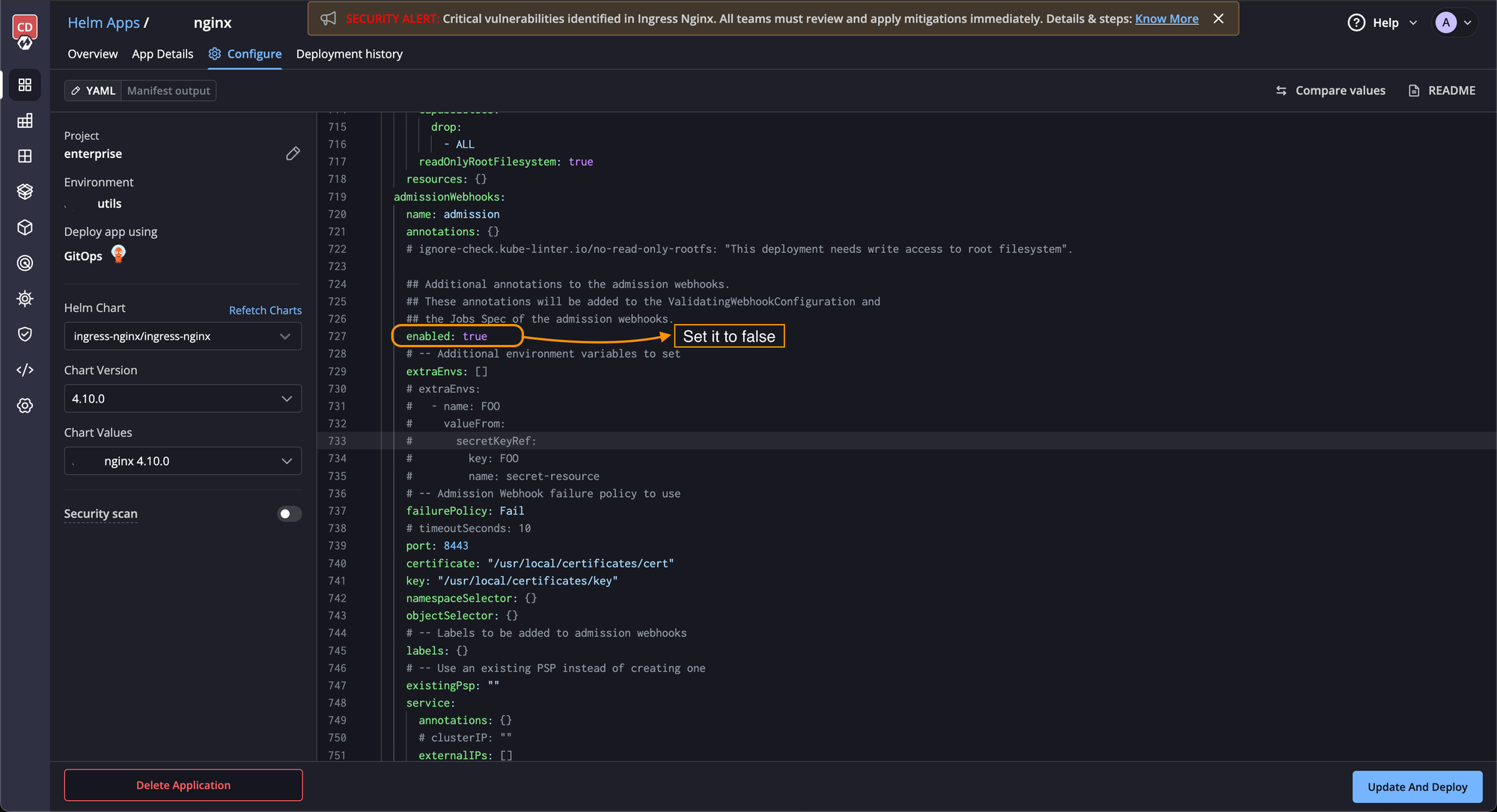
For Helm Installations
If you have installed Ingress nginx controller using helm cli, then execute the following commands to upgrade:
helm upgrade ingress-nginx ingress-nginx/ingress-nginx --reuse-values --set controller.admissionWebhooks.enabled=false --version <your current nginx chart version>For kubectl Installations
- Delete ValidatingWebhookConfiguration
- Remove
--validating-webhookargument from the controller container
Note:- Deactivating admission webhooks removes crucial ingress validation checks, which could result in multiple ingresses with overlapping host and path configurations being accepted, leading to unpredictable routing behavior.
Permanent Mitigation
Update to Ingress NGINX Controller versions 1.12.1 or 1.11.5. This is the most straightforward and comprehensive permanent mitigation.
Important Considerations
- Re-enable the Validating Admission Controller after upgrading
- Regularly audit and update your Kubernetes infrastructure
Network Security Recommendations
- Enforce strict network policies
- Limit admission controller access to Kubernetes API Server
- Temporarily disable the admission controller if immediate upgrade isn't possible
Conclusion
The discovered Ingress NGINX vulnerabilities underscore the importance of proactive security management in Kubernetes environments. Prompt action, careful verification, and strategic mitigation are key to protecting your clusters.
FAQ
What are the recent vulnerabilities in Kubernetes Ingress NGINX?
Recent high-severity flaws allow attackers to exploit misconfigurations, potentially leading to privilege escalation or data exposure
Which versions of Ingress NGINX are affected?
Multiple versions are impacted; users should check the official CVE listings and update to the patched versions immediately.
How can I mitigate these vulnerabilities?
Apply the latest security patches, audit ingress configurations, and follow official security advisories for hardening steps.
Why is it critical to act quickly?
Delays in patching can expose clusters to real-world attacks, especially in production environments with public-facing services.
References
Official CVE Links:
Kubernetes Official Documentation
Vigilance is Your Strongest Defence in Cloud Native Security







