1. Access management ensures secure and controlled access to Kubernetes resources and DevOps workflows.
2. Native Kubernetes RBAC (Role-Based Access Control), though powerful, can be complex, static, and difficult to scale across multiple clusters.
3. Devtron simplifies access management with a user-friendly interface, fine-grained permissions, SSO integrations, and role-based governance.
4. Organizations can leverage permission groups, role hierarchies, and Kubernetes resource-specific access for enhanced security.
5. Future-ready with Devtron’s upcoming Agentic AI feature that will bring intelligent automation into access governance.
What is Access Management?
Access management is the process of defining, controlling, and monitoring who can access applications, systems, and resources, and what actions they are allowed to perform. It ensures security, compliance, and accountability in modern DevOps workflows.
In the context of Kubernetes, access management revolves around RBAC (Role-Based Access Control). While Kubernetes RBAC is flexible and powerful, it often introduces challenges when scaling across multiple clusters and teams.
Challenges of Native Kubernetes Access Management
Though Kubernetes has a robust RBAC-based access management system, it comes with limitations:
1. Complexity and Learning Curve
- RBAC requires defining roles, subjects, bindings, and policies across multiple namespaces and clusters.
- For organizations with diverse teams and large user bases, maintaining RBAC can be overwhelming.
2. Static Authorization
- Kubernetes RBAC rules are static. Updating roles and permissions requires manual intervention.
- This becomes a bottleneck in dynamic DevOps environments where teams and responsibilities frequently change.
3. Limited Integration with Identity Providers
- Kubernetes RBAC works best with internal cluster-defined identities.
- Integrating external identity providers like LDAP, SAML, or cloud IAMs requires additional tools and complex setups.
Simplifying Access Management with Devtron
Devtron, a comprehensive Kubernetes management and DevOps platform, eliminates RBAC complexity by offering:
- User-based access management (role-based permissions with intuitive UI).
- SSO Integration with Google, GitHub, GitLab, OpenID Connect, etc.
- Fine-grained access control down to project, environment, and Kubernetes resource level.
- Permission groups for easy bulk permission assignment and governance.
User Management on the Devtron Platform
With Devtron’s access management system, administrators can:
- Define user roles and permissions (View only, Build & Deploy, Manager, Admin, Super Admin).
- Assign SSO-based authentication for secure login and centralized control.
- Onboard/offboard users quickly, ensuring compliance in access provisioning and de-provisioning.
Kubernetes Resource Access with Devtron
In the fast-paced world of DevOps, managing user access and permissions is critical for maintaining security and efficiency in the software delivery pipeline. Devtron, a comprehensive DevOps platform, offers a powerful user-based access management system that allows organizations to control and govern user access to various components and functionalities within the platform.
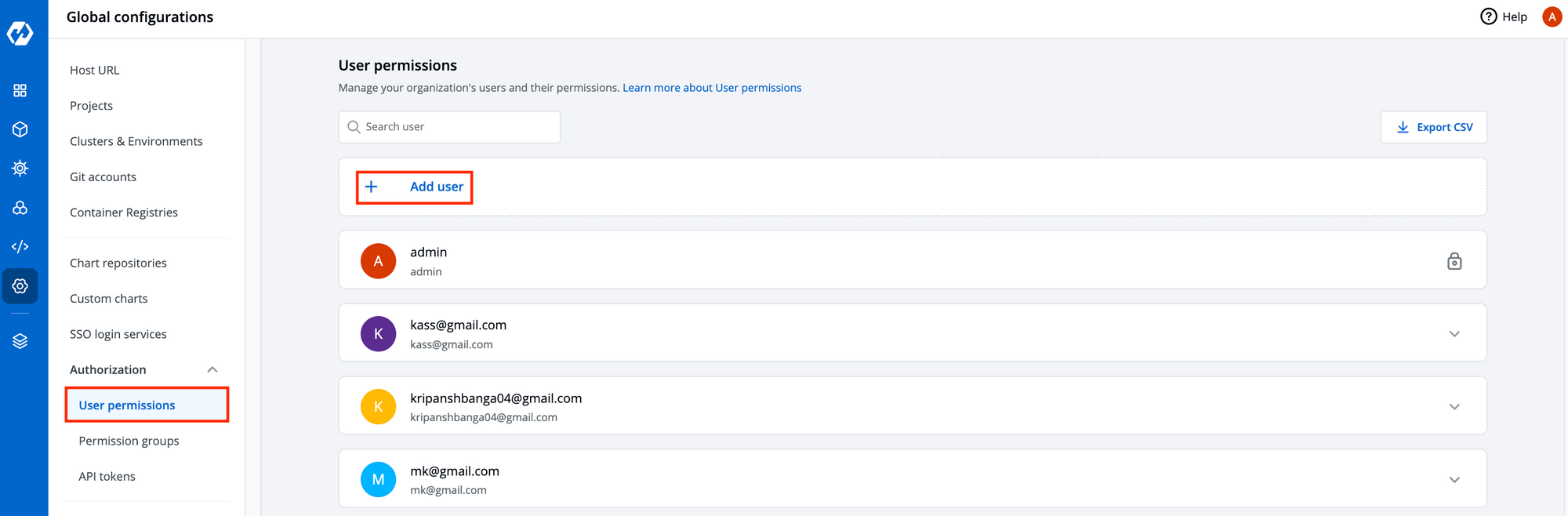
Adding Users
To add a new user in Devtron, the first step is to configure Single Sign-On (SSO) login, which ensures secure authentication. Once SSO is set up, administrators can navigate to the global configuration settings and access the "Authorization" section. From there, they can proceed to the "User Permissions" tab and add new users.
Administrators can also assign custom applications, such as the Helm application, Kubernetes resource browser, or chart groups, to the user during the user creation process. Additionally, administrators can define user roles, such as view, build and deploy, based on their responsibilities and job functions.
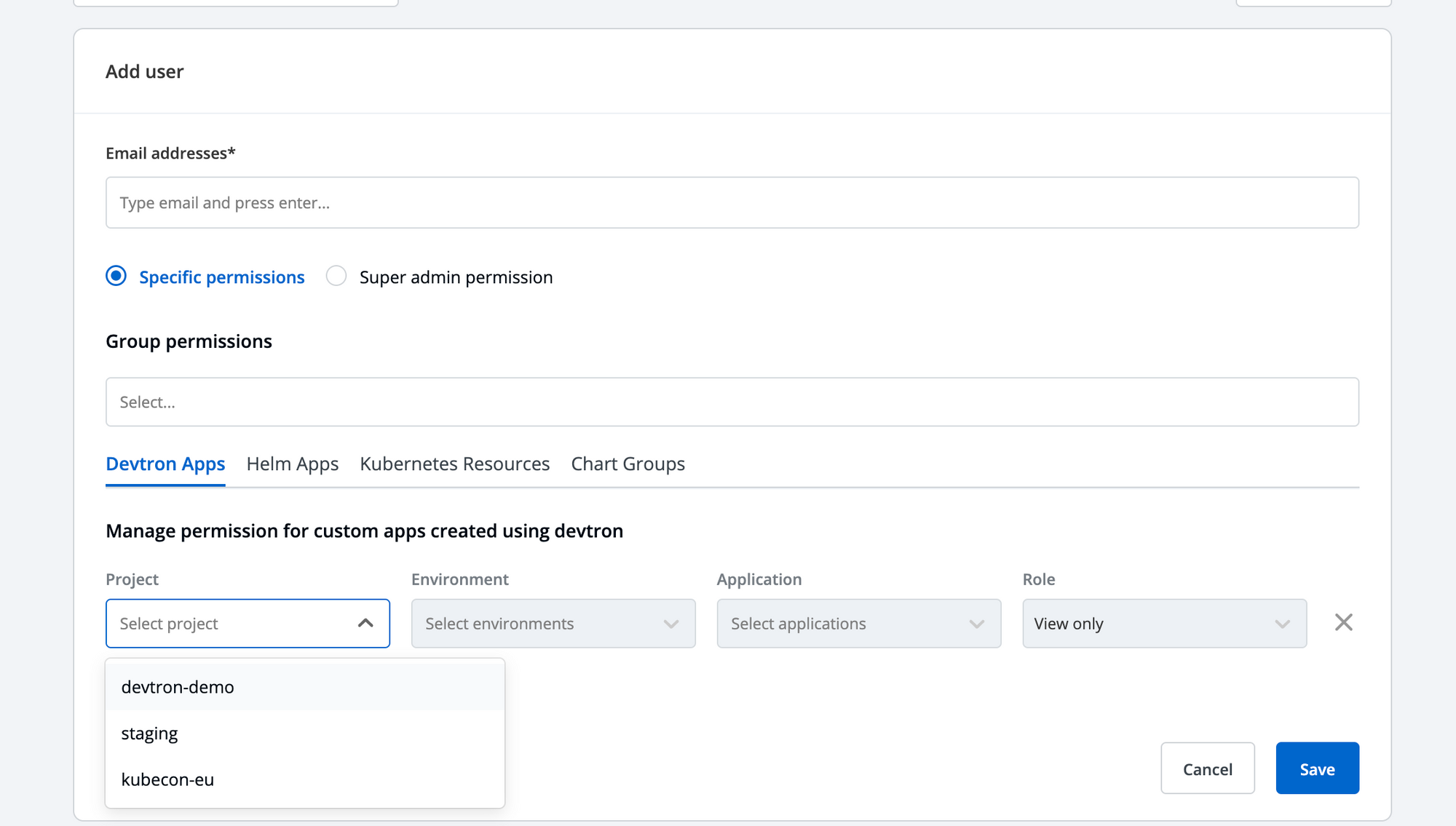
Fine-Grained Access Management
Devtron offers refined access management capabilities, allowing administrators to provide fine-grained access to users. This is achieved by selecting the project to which users should have access, followed by specifying the environment and custom application within the project. By configuring permissions at this level, organizations can ensure that users only have access to the specific resources they need, enhancing security and minimizing the risk of unauthorized access.
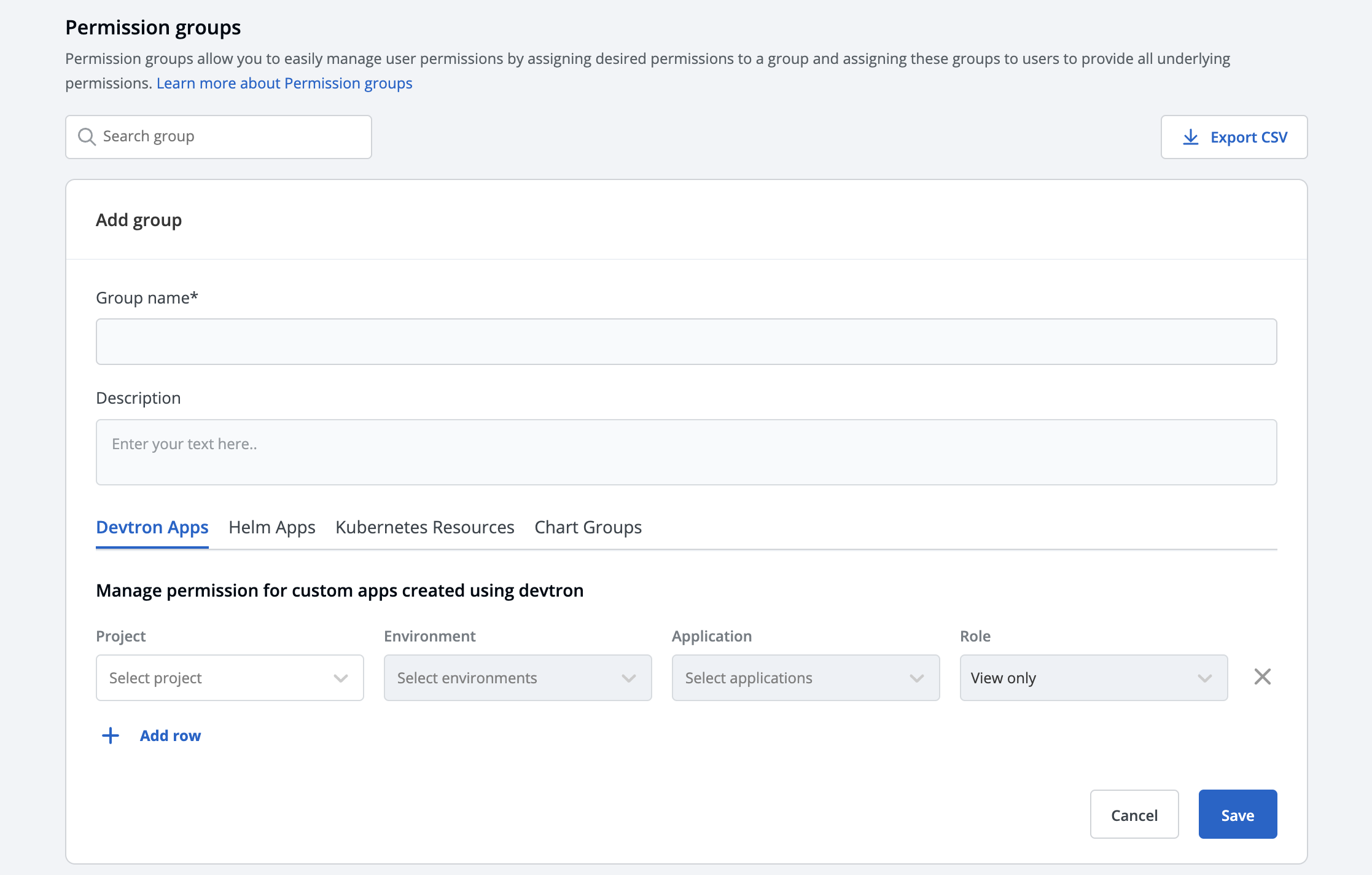
Permission Groups for Streamlined Access
To simplify access management, Devtron allows administrators to create permission groups. These groups can be associated with specific permissions, and users can be added to the groups, simplifying the process of managing permissions for multiple users. Assigning permissions to groups rather than individual users helps maintain consistency and streamlines access management as user roles and responsibilities change over time.
Kubernetes Resource Access
A noteworthy feature of Devtron's access management is the ability to provide users access to specific Kubernetes resources. Administrators have granular control over resource permissions by selecting the namespace, apiGroups, Kind, and ResourceName. These permissions are reflected within the Kubernetes resource browser, ensuring that users only see and interact with the resources they are authorized to access.
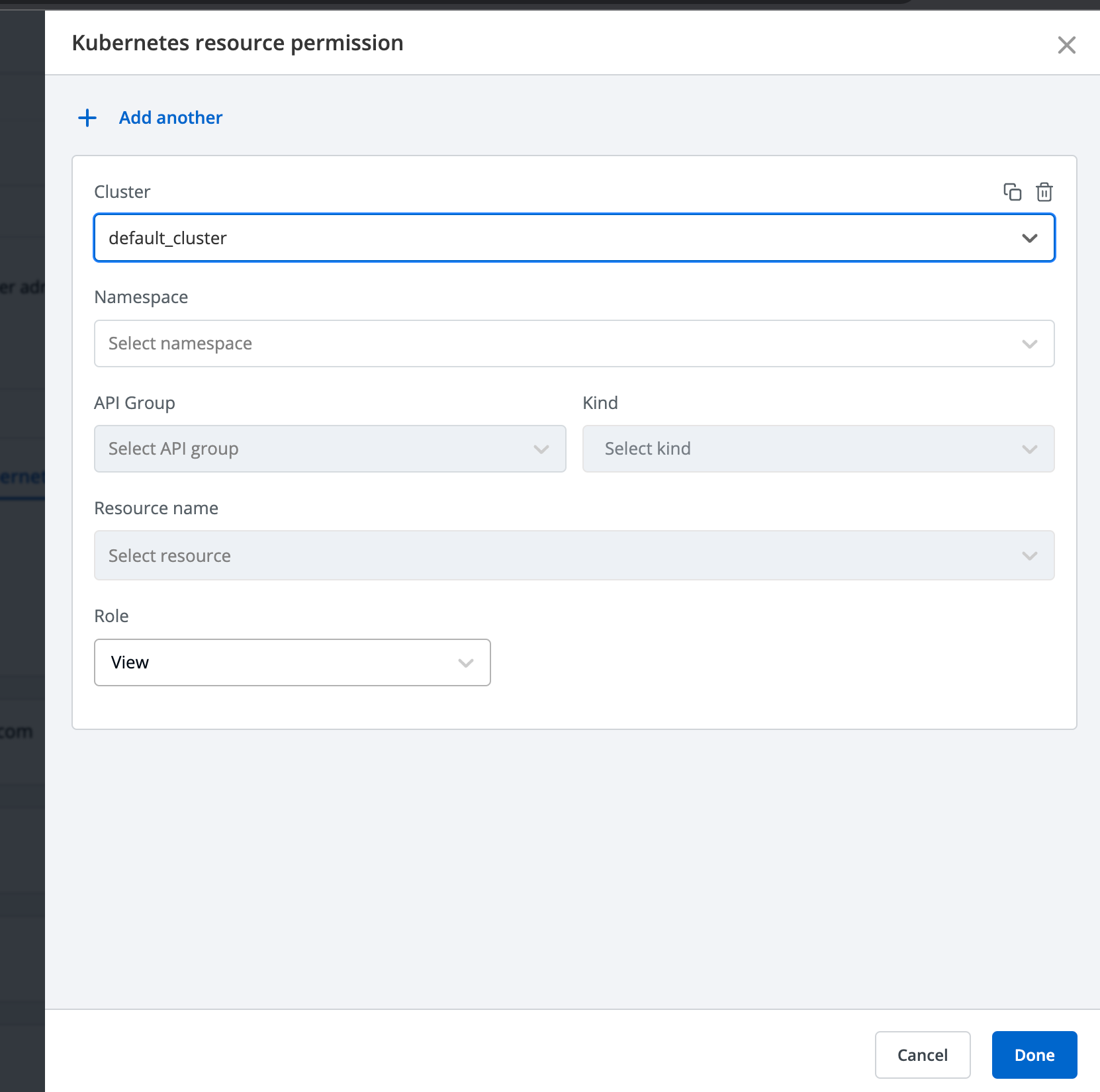
We can provide a user access to the Kubernetes resources. Administrators can choose the namespace, apiGroups, Kind, and ResourceName.
The permissions for the Kubernetes resources will be reflected in the kubernetes resources browser.
How Devtron Improves Access Management Beyond RBAC
- UI-driven access controls reduce reliance on complex YAML configs.
- Dynamic updates to roles and permissions without downtime.
- Integration with identity providers and SSO for enterprise-wide consistency.
- Audit-friendly logs and activity tracking for compliance reporting.
Conclusion
Access management is the backbone of secure Kubernetes operations. While native RBAC provides the foundation, it struggles with scalability, usability, and integration.
Devtron’s access management system enhances this by providing:
- Fine-grained, role-based controls.
- Seamless SSO integration.
- Permission groups and resource-level access.
- A simplified, intuitive interface for managing multi-cluster security.
With Devtron, organizations can achieve secure, collaborative, and scalable DevOps workflows without the burden of maintaining complex RBAC rules manually.







