Kubernetes clusters are central to the development and operation of cloud-native applications, offering scalability, flexibility, and robust management features. As these clusters become integral to more businesses, the importance of securing them cannot be overstated. Cybersecurity in Kubernetes is crucial, given the sensitive data and critical processes they often handle.
The focus on security brings air-gapped deployments into the spotlight. This method involves isolating Kubernetes clusters from the public internet, significantly reducing the risk of cyber attacks. In this discussion, we'll explore how air-gapping not only strengthens the security of Kubernetes environments but also ensures the safety of the applications running within them.
Understanding Air-Gapped Deployments
Air-gapped deployments are a security measure where a computer or network is physically isolated from unsecured networks, especially the internet. This means there's no direct connection between the air-gapped system and any external network, making it virtually impossible for hackers to access.
The Role of Air-Gapped Environments in Enhancing Kubernetes Security
In the realm of Kubernetes security, air-gapped environments play a crucial role in fortifying defenses against a spectrum of cyber threats. These deployments are specifically designed to shield against malware, ransomware, and unauthorized intrusions by hackers. By eliminating direct internet access, air-gapped deployments effectively close the door on the most common attack vectors used by cybercriminals to exploit vulnerabilities within systems.
Malware and ransomware, malicious software designed to damage or gain unauthorized access, rely heavily on network connectivity to infiltrate and spread within systems. Air-gapped environments, by their very nature, prevent such threats from reaching critical Kubernetes clusters by ensuring there is no pathway for these malicious entities to propagate. This isolation builds a proverbial wall around your sensitive data and applications, where the only way in or out is through strictly controlled and monitored access points.
Furthermore, the significance of air-gapped systems extends beyond just malware prevention. In an era where data breaches are increasingly common, the physical separation provided by air-gapped deployments is a robust security measure against unauthorized access from the public internet. Hackers often exploit network vulnerabilities to gain unauthorized access to sensitive information. Air-gapped environments, devoid of direct external network connectivity, significantly reduce the surface area for such cyber attacks, making it exceedingly difficult for unauthorized entities to penetrate the security perimeter.
Key Components of Air-Gapped Deployments in Kubernetes
In the context of air-gapped deployments in Kubernetes, certain key components are essential for maintaining the security and functionality of the system. Two critical aspects of these deployments are the management of upgrades and the maintenance of repositories, both of which require careful handling to ensure the integrity of the air-gapped environment.
Managing Upgrades
Upgrades are vital for keeping software secure and functional, addressing vulnerabilities and introducing new features. However, in an air-gapped environment, the standard online update mechanisms are not available. This necessitates a manual process of downloading updates to a secure, internet-connected machine, then transferring these updates to the air-gapped environment using physical media. This method ensures that the Kubernetes clusters and their workloads can be kept up-to-date without exposing them to the risks associated with direct internet access.
Maintaining Repositories
For Kubernetes deployments, container images (often Docker) and other dependencies are typically stored in repositories. In an air-gapped setting, it's crucial to have a local copy of these repositories within the isolated network and cut off from the outside world. This allows for the continued deployment and scaling of applications without needing to fetch resources from external sources. Regularly updating these local repositories with the latest secure versions of software and dependencies is a key part of maintaining the security posture of the environment.
Use of Physical Media
Physical media, such as USB drives, play a pivotal role in the update process within air-gapped deployments. They are used to transport updates, container images, and other critical data into the air-gapped environment. The use of physical media requires strict security protocols to prevent the introduction of malware or other security threats into the isolated network.
Role of Firewalls
While air-gapped deployments are isolated from the internet, they still require internal network connectivity to function. Firewalls are crucial in this setup, as they help to enforce network security policies and prevent unauthorized access, even from within the organization. By carefully configuring firewall rules, administrators can ensure that only legitimate traffic is allowed, further enhancing the security of the air-gapped Kubernetes deployment.
Security Practices for Air-Gapped Kubernetes Clusters
Implementing robust security practices is paramount for air-gapped Kubernetes clusters, given their use in environments where the highest levels of data protection are required. These clusters, by design, are insulated from many external threats due to their lack of direct internet connectivity. However, this does not negate the need for comprehensive internal security measures.
Physical Access Controls
One of the foundational security measures for air-gapped Kubernetes clusters is controlling physical access to the hardware and storage media. This involves securing the physical premises where servers are located, using locks, biometric scanners, and surveillance systems to prevent unauthorized access. Such controls ensure that only authorized personnel can interact with the systems, significantly reducing the risk of insider threats or physical tampering.
Local Area Network (LAN) Security
While air-gapped clusters are isolated from the wider internet, they still operate within a local area network (LAN). Securing this LAN is crucial to prevent lateral movements by potential intruders who might gain access to the internal network. This includes implementing network segmentation to limit the blast radius of any potential breach, using firewalls to control traffic between segments, and employing network monitoring tools to detect suspicious activities.
Prevention of Malware
Despite the isolation provided by air-gapping, malware can still potentially enter through removable media or compromised hardware. To mitigate this, strict policies and scanning procedures for any external device or media that interacts with the air-gapped environment are necessary. This includes regular scanning of USB drives, external hard drives, and other media with up-to-date antivirus software before they are connected to the air-gapped network.
Protection of Critical Systems and Sensitive Information
Air-gapped Kubernetes clusters are often employed to protect critical systems and sensitive information that, if compromised, could lead to significant financial, reputational, or operational damage. Hosting these systems on-premises within air-gapped environments provides an additional layer of security, as physical and network access can be tightly controlled. This setup is particularly beneficial for industries like finance, healthcare, and government, where the confidentiality and integrity of data are paramount.
Role of Disaster Recovery
Even in air-gapped environments, disaster recovery plans are essential to ensure business continuity in the event of data loss, system failures, or other unforeseen incidents. This involves regular backups of critical data, which should be stored securely and, ideally, off-site to prevent simultaneous loss in case of physical disasters. Effective disaster recovery strategies ensure that, even in the worst-case scenarios, systems can be restored and data loss minimized.
Devtron and Air-Gapped Deployments: A Secure Partnership
With Devtron, we provide a comprehensive suite of tools tailored for Kubernetes, transforming air-gapped deployments from a complex challenge into a streamlined, efficient process. Our platform is engineered to make deployment of software into environments without internet access not just possible, but straightforward and secure. This is all made possible through our “virtual cluster” technology.
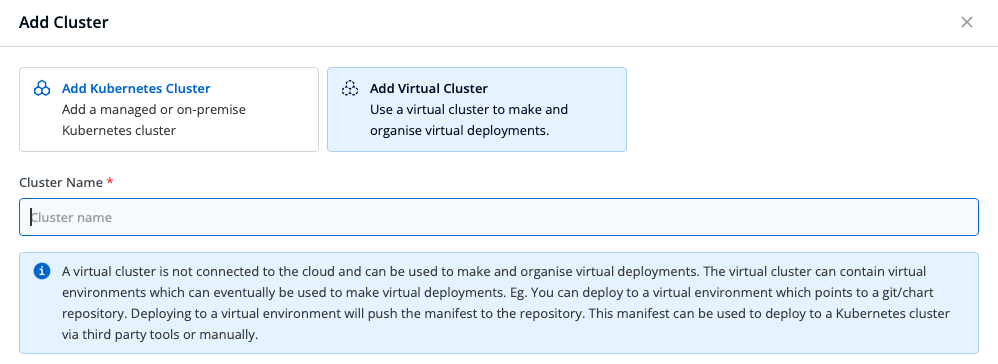
Our approach to enhancing security in air-gapped deployments is multifaceted. Through automation, we ensure that security policies are consistently applied and that updates are conducted in a timely manner, greatly reducing the potential for human error. Our role-based access controls (RBAC) offer detailed management capabilities, allowing you to precisely dictate who has access to various resources, thereby significantly lowering the risk of unauthorized access.
Furthermore, our lifecycle management features are essential for keeping applications and their dependencies up-to-date with the latest security patches, a critical aspect in air-gapped environments where traditional online updates are unavailable. This ensures that your Kubernetes deployments remain secure, compliant, and operational, overcoming the unique challenges posed by the lack of internet connectivity. Learn more about our suite of solutions today.