Are you confident enough that your containers are secure from potential threats?
The containers are lightweight virtual machines that encapsulate applications along with their dependencies and enable efficient execution of applications across different environments. Containers have revolutionized the way software is developed, packed, and deployed. The adoption of containerized applications has skyrocketed driven by the need of organizations for flexibility and scalability in their software delivery pipelines.
However, as with any technology, a container does come with potential risks and vulnerabilities. If your container has insecure configurations, outdated components, or vulnerabilities in the base image it is more likely that your application will get exposed to threats like data breaches, unauthorized access, and denial of service (DOS/DDOS).
This blog post will delve into the world of container vulnerabilities. We will look at what can cause your container to be vulnerable and how to address these vulnerabilities in a Devtron way and secure your applications in production.
Container vulnerabilities can have severe consequences, but they don't necessarily originate from the container itself. These vulnerabilities might even originate from the application code running within the container. To address these risks, it's essential to understand the most common vulnerabilities and implement effective mitigation strategies.
Devtron's comprehensive platform can help you detect and remediate common container vulnerabilities, safeguarding your applications across all stages of development and deployment.
Most Common Vulnerabilities
- Outdated Dependencies: This vulnerability's roots can be traced to our application's code files. Where the intricate code of our application utilizes multiple dependencies, these dependencies can be outdated and have some vulnerabilities that often get overlooked during development.
E.g. In 2021, security researchers discovered a vulnerability in the widely used Log4j logging library. This library is one of the most used libraries for Java applications. This library has a vulnerability, if exploited, the attacker can take access to your “Shell”. All the applications using this library were on the edge of hitting destruction. Read more for detailed information, check this blog. - Vulnerable Base Image: The base image of the Operating System (OS) in the container that’s running our application can have the vulnerability. These images may contain some packages with vulnerabilities that attackers can exploit.
E.g. In 2020, a vulnerability in the official Alpine Linux Docker image was discovered. It allowed attackers to gain root access within containers using the base image. Due to this vulnerability, many popular images were affected as this was the base image for their application. - Misconfigured Containers: These vulnerabilities are mostly unknowingly generated by humans. While setting up the configuration for the application environment developers can end up leaving some container ports open.
E.g. In 2018, Tesla faced an incident where the cloud resources of Tesla were used for crypto mining. The attacker got access to the Kubernetes dashboard of Tesla which was unprotected and used the cloud resources for mining crypto. Read more for detailed information - Vulnerability in Host System: Vulnerability in the Host System refers to the vulnerability in the underlying infrastructure. The same infrastructure on which our container runtime (e.g. Docker) or containerized application is running.
E.g. In 2019, a vulnerability in runC container runtime was detected. runC is a container runtime originally developed by Docker and later extracted as an open-source library. By exploiting the vulnerability the attackers were able to gain root access to the local system using containers. Read more for detailed information

Vulnerability Management with Devtron
Now that we understand the most common vulnerabilities, let's explore ways to mitigate them and prevent potential disasters. To address these vulnerabilities, we should proactively scan for and fix them before deploying the application to production. We can identify and remediate issues early by incorporating vulnerability scanning into our development and deployment processes, ensuring a more secure and robust application.
Although numerous tools exist for vulnerability scanning at various stages, coordinating multiple vulnerability scanning tools and seamlessly integrating them into your application workflow can pose a significant challenge. Each tool typically requires a separate configuration, adding complexity to the process. For instance, setting up Sonarqube for static code analysis, configuring Trivy or Clair for container scanning, and utilizing Codacy for security checks all demand individual setup procedures. This fragmented approach can complicate the management of vulnerability scanning across various stages of development.
To streamline the vulnerability scanning process and avoid the complexities of configuring various tools, Devtron offers a single dashboard that enables you to manage multiple vulnerability scanning tools within your application's workflow. With Devtron, you can seamlessly integrate available tools that will scan your application at every stage of the workflow, alerting you to any vulnerabilities within your codebase.
Devtron also provides a feature to scan Kubernetes resources and a security policies feature to govern the deployment of your applications. The security policies feature allows you to define policies for security at different levels – global, cluster, or even application level. By defining these policies, you can control the deployment of your application to production environments, ensuring that only compliant applications are deployed.
Devtron's vulnerability management capabilities extend across the entire software development lifecycle, from pre-CI and post-CI stages to post/post-deployment phases. Let's explore how Devtron can help you maintain a secure application at every step.
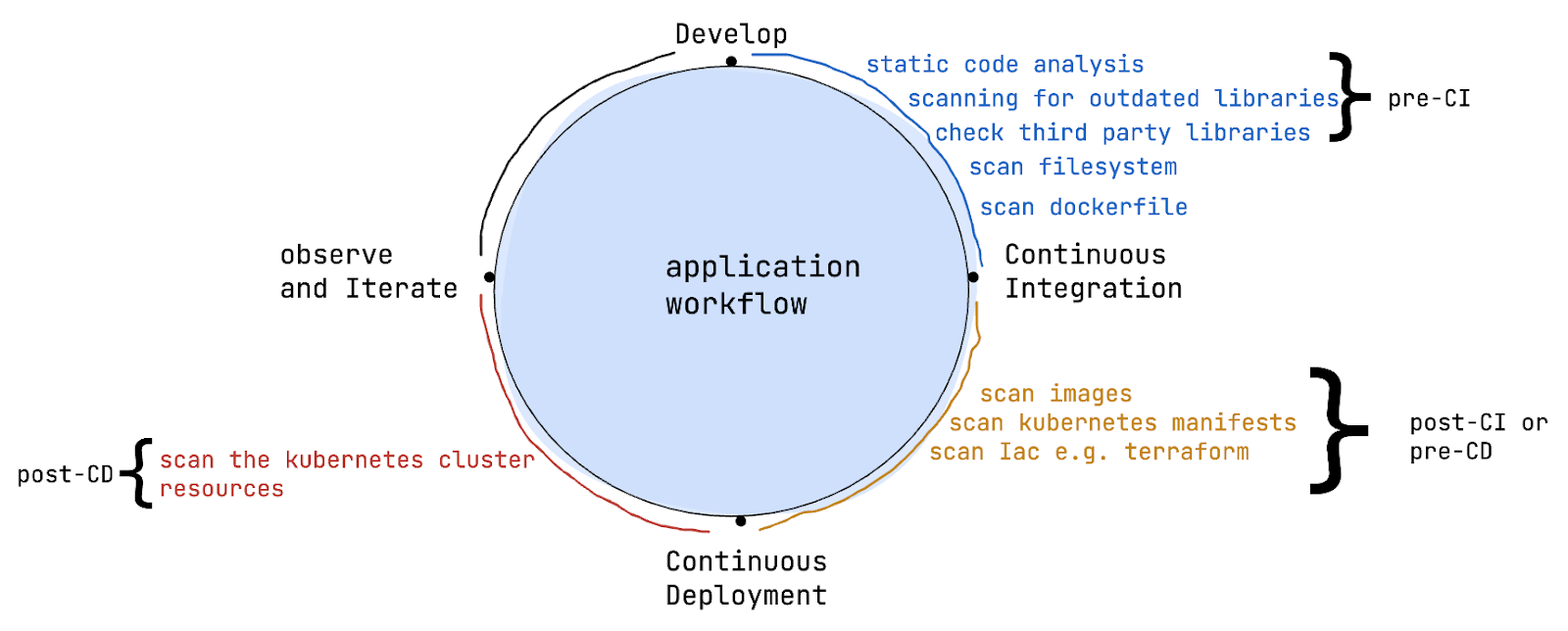
Pre-CI Stage (Code Scanning)
At the pre-CI stage, Devtron offers seamless integration with renowned static code analysis tools such as Semgrep and SonarQube. These powerful tools scan your application's codebase, pinpointing potential vulnerabilities well before the container image is built. Catching and rectifying vulnerabilities early in the development cycle, not only streamlines the process but also secures your codebase's security posture. With Devtron's user-friendly interface, configuring these tools is a breeze—all you need to do is add a plugin.
To add any plugin, move to workflow editor, build pipeline, and during build pipelines configuration, you can add any plugin that you want to add. For more details about the plugins, feel free to check out our documentation on pipeline plugins.
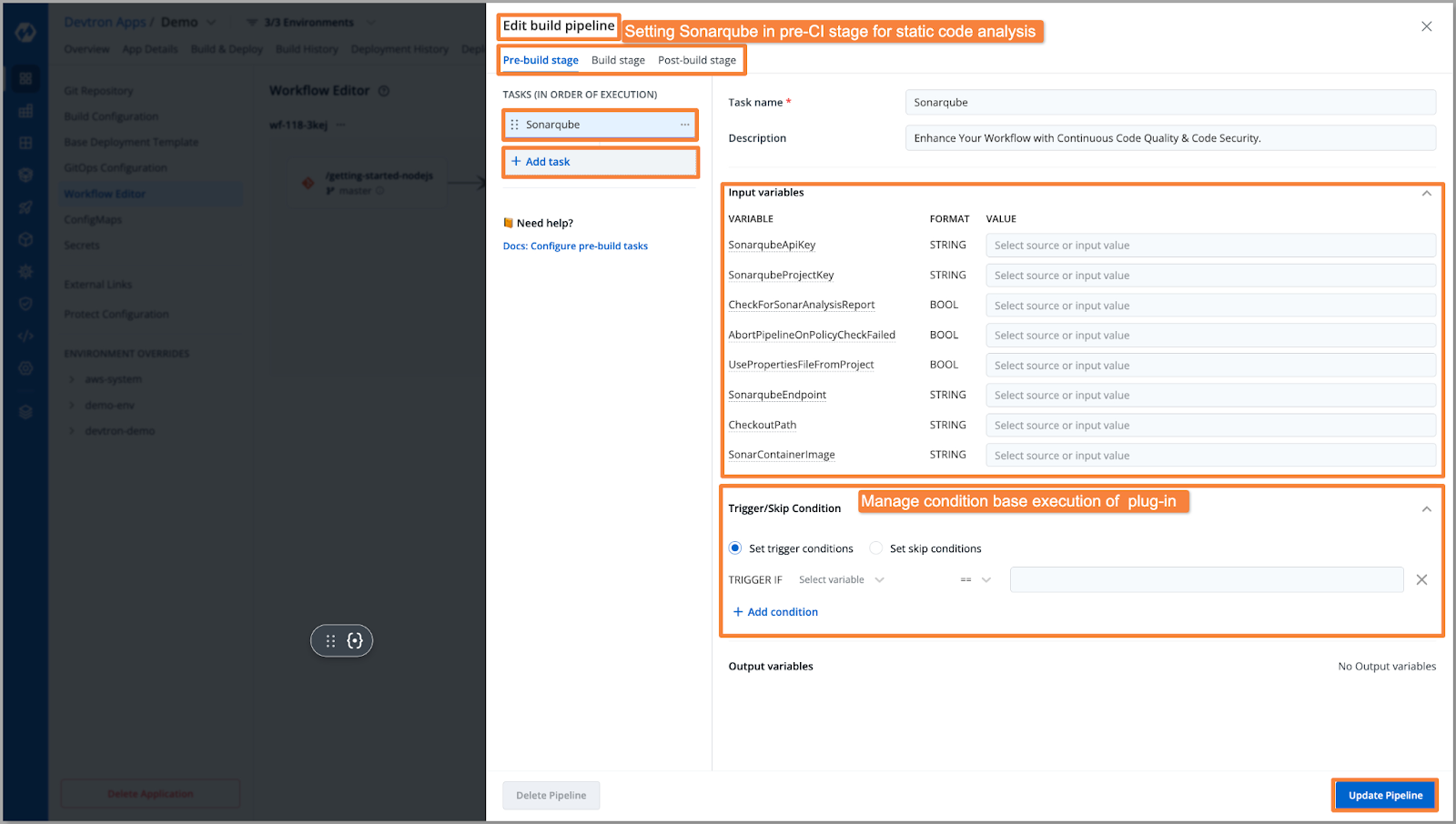
For setting up the Sonarqube, select the plugin and you will be able to see the entire configurations as shown in the below image. Provide the necessary information, and it will automatically scan the source code and send the results to the provided Sonarqube dashboard.
Post-CI Stage (Container Image Scanning)
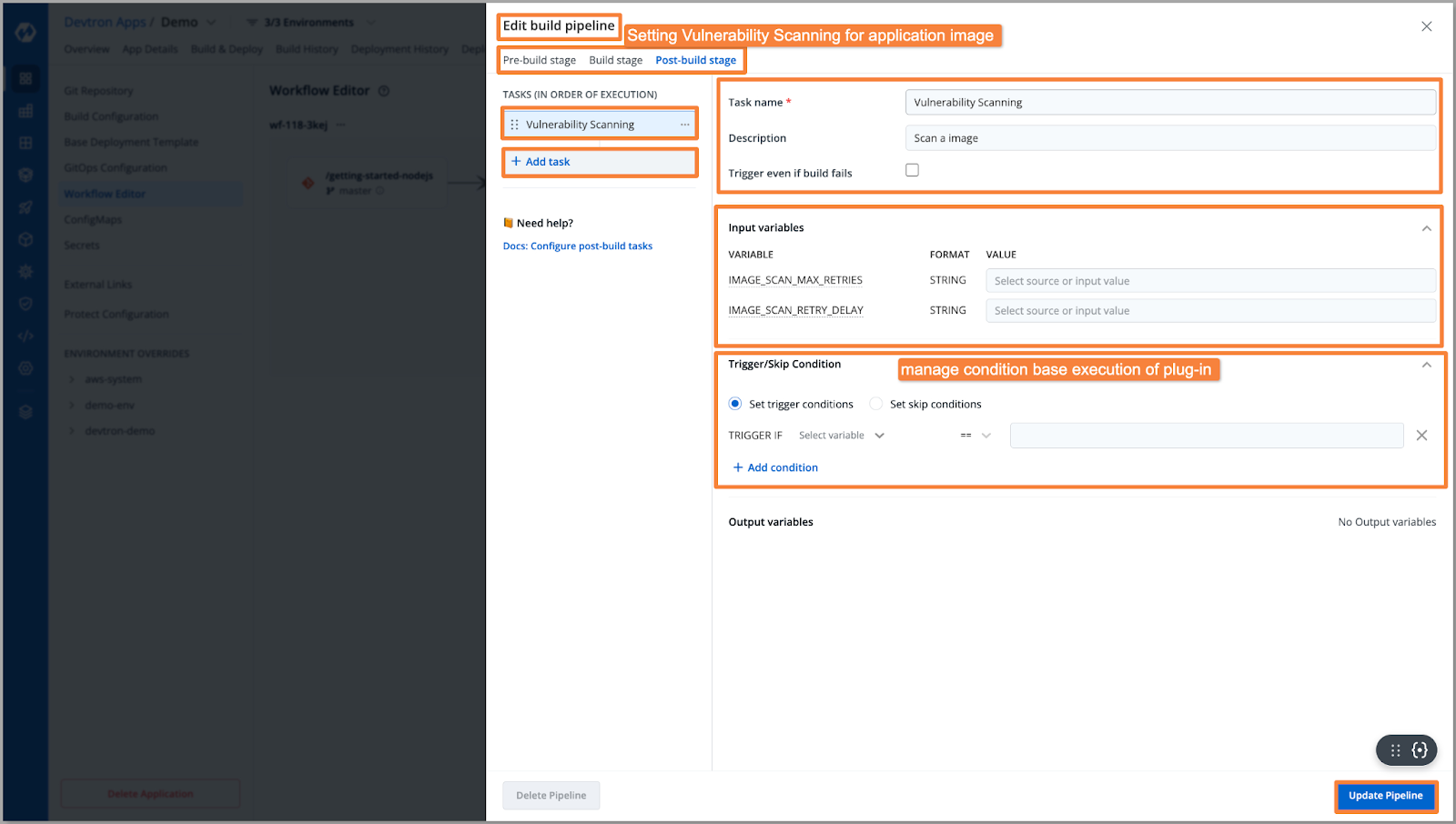
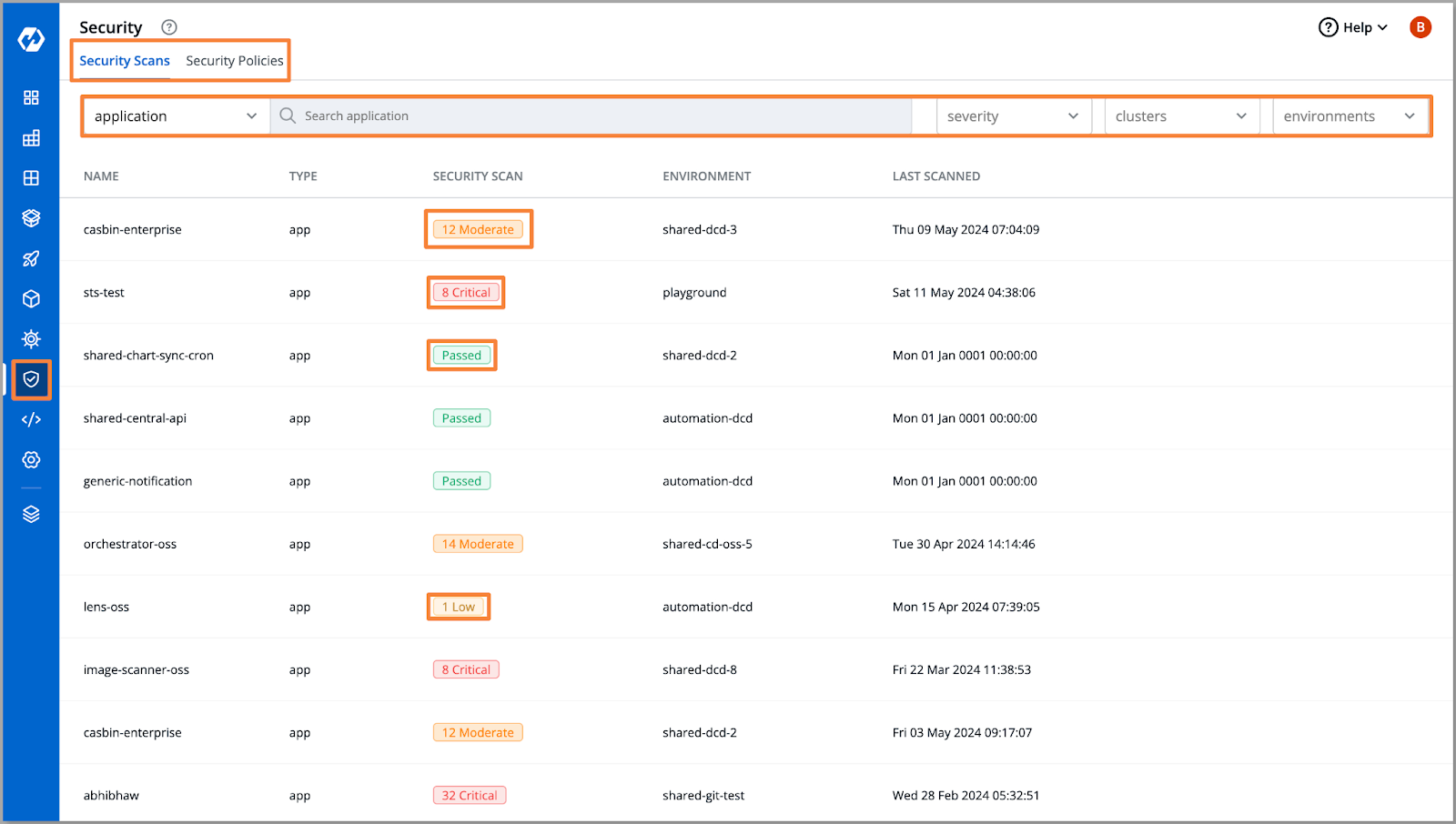
After the code is compiled into a container image, Devtron employs a vulnerability scanning plugin, leveraging Trivy's capabilities to scan the image. These tools analyze the container layers and dependencies for any known vulnerabilities. Devtron then presents the scan results, enabling you to promptly identify and rectify vulnerabilities before proceeding to push the image to the registry.
Vulnerabilities are categorized based on severity levels—ranging from low to moderate and critical. With Devtron's security policies in place, appropriate actions can be taken accordingly. For instance, if a critical vulnerability is detected, the image will not advance to the deployment stage, mitigating the risk of potential disasters.
Additionally, Devtron offers the Copacetic plugin, which aids in addressing outdated dependencies. By tracing the CVE numbers associated with vulnerabilities, Copacetic facilitates the retrieval of fixed versions, simplifying the process of resolving security issues.
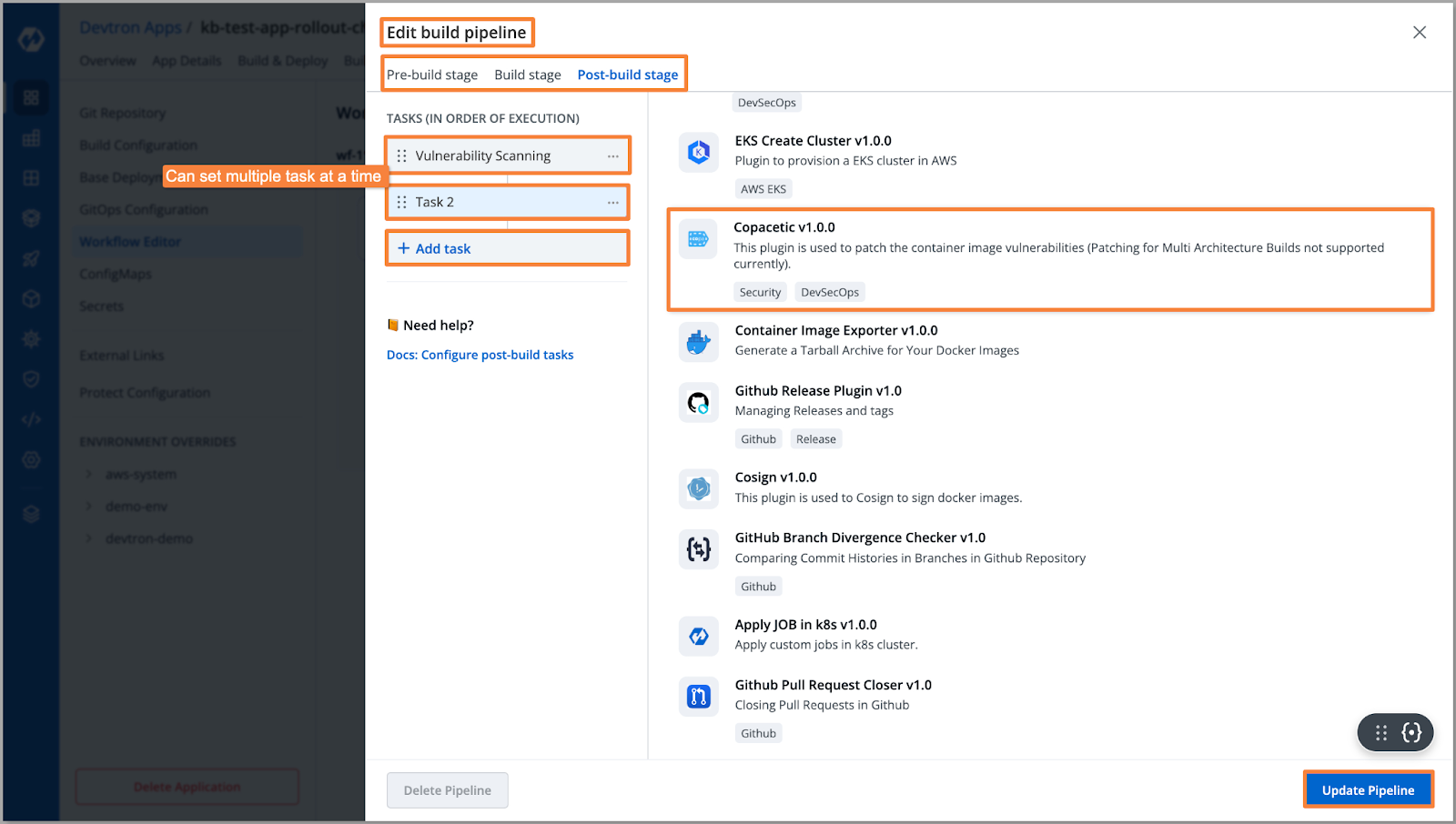
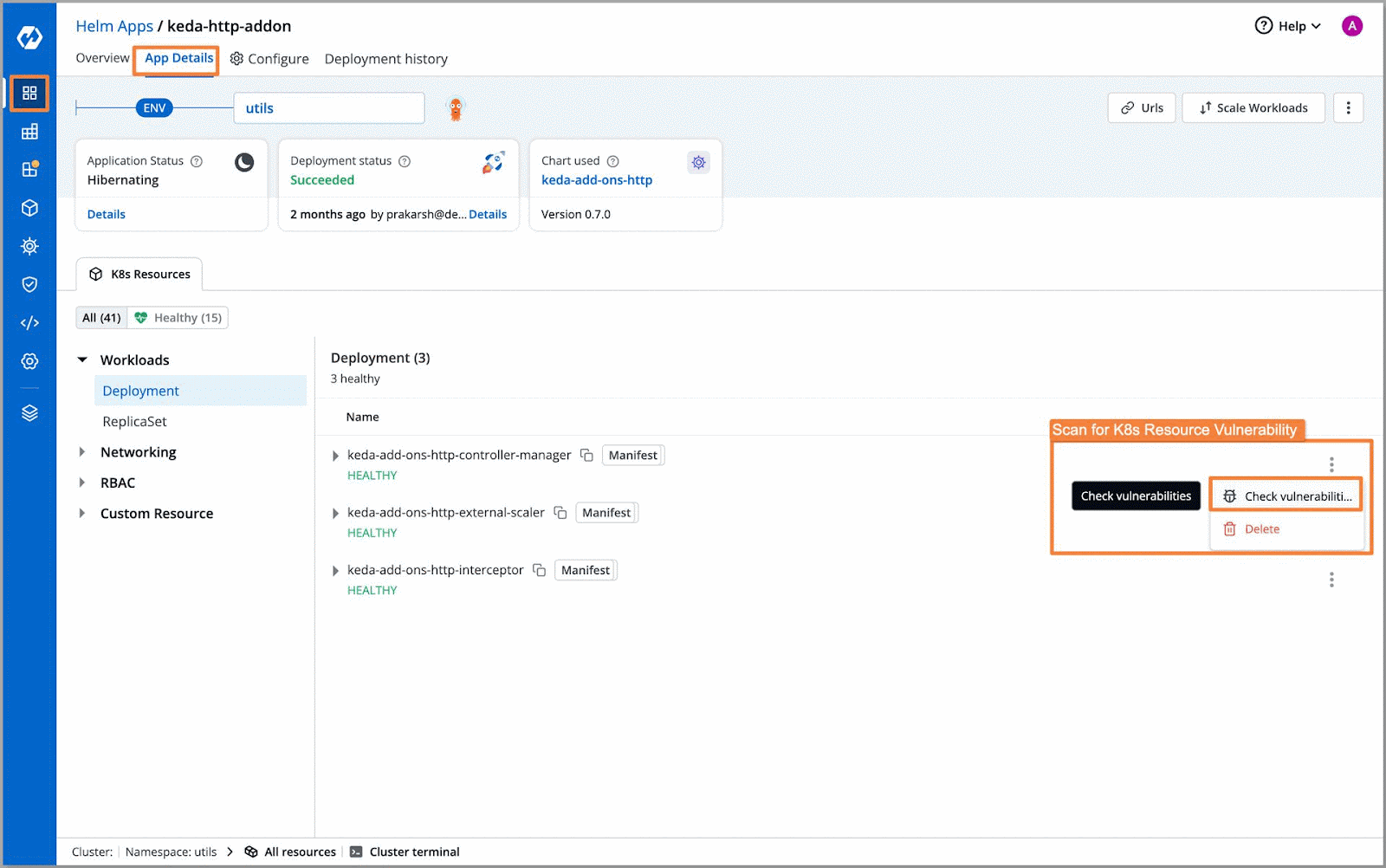
Post-Deployment Stage (Runtime Scanning)
Devtron doesn't stop its vigilance post-deployment. It seamlessly integrates with runtime security tools, enabling the scanning of your live containers and workloads for any potential vulnerabilities or threats. Furthermore, Devtron's vulnerability scanner, powered by Trivy, continuously monitors your application for vulnerabilities, extending its scope to include scanning Kubernetes resources. This comprehensive approach ensures that your application remains resilient against evolving security challenges.
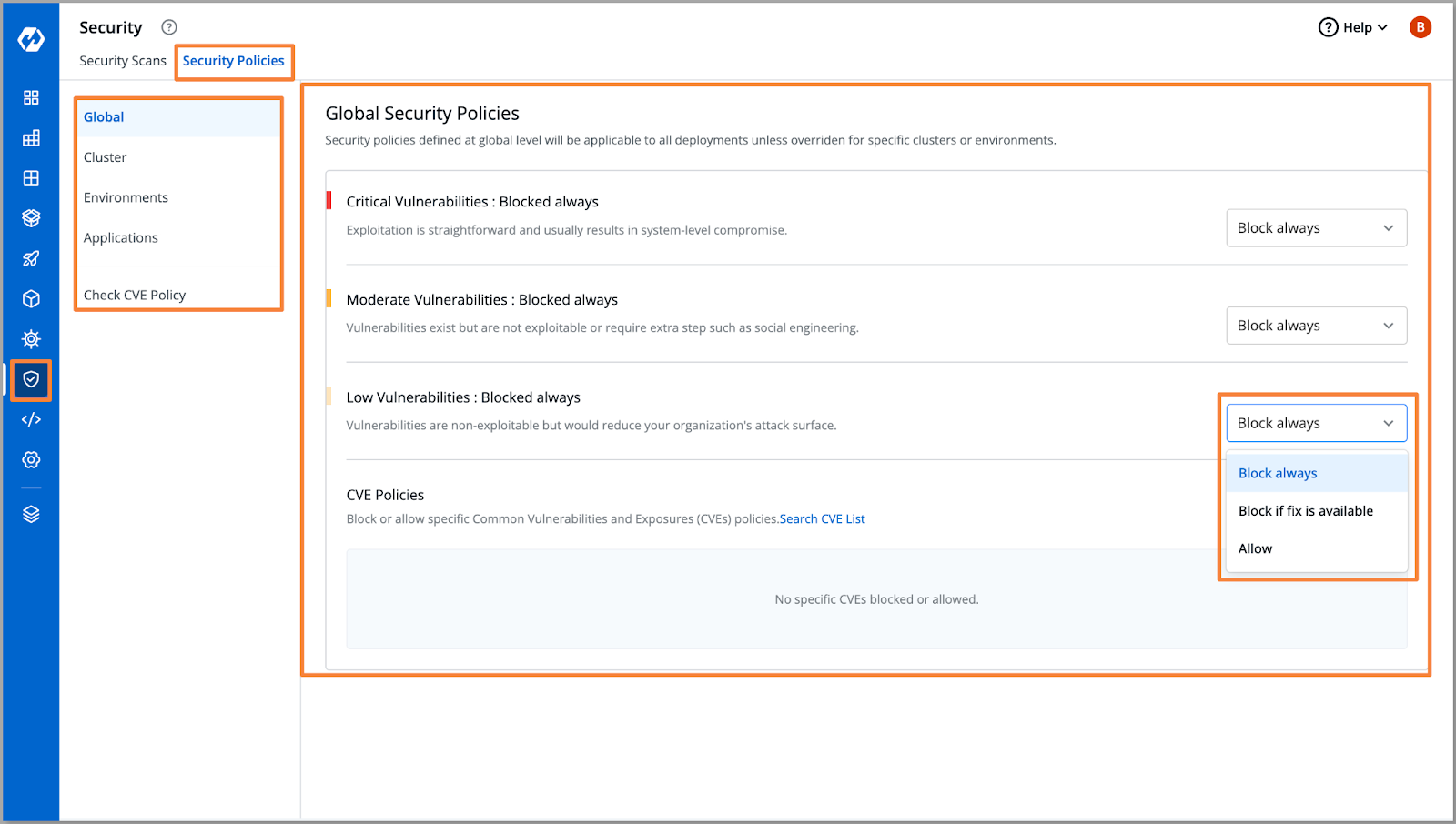
Security Policies
Devtron's security policies feature allows you to define policies at the global (i.e. all clusters on devtron), cluster, or application level. These policies govern the deployment of your applications based on the severity of vulnerabilities found during the scanning process. For example, you can set a policy to prevent the deployment of applications with critical vulnerabilities.
Devtron stands out from other software delivery platforms with DevSecOps as its one of the core pillars. It provides an intuitive dashboard that seamlessly integrates multiple industry-leading vulnerability scanning tools into a single workflow. This centralized approach not only streamlines the process but also reduces complexity. Moreover, Devtron empowers you with the ability to define custom security policies and automate actions based on vulnerability severity, ensuring that only secure applications make it to production. Its comprehensive end-to-end vulnerability scanning capabilities span the entire software development lifecycle, from pre-CI to post-deployment, providing a robust and holistic approach to vulnerability management. With the flexibility to leverage popular tools like Semgrep, SonarQube, Trivy, Clair, and Copacetic, Devtron offers a powerful yet user-friendly solution tailored to your specific needs, ultimately delivering a more secure and efficient application delivery pipeline.

Conclusion
We know containers are an efficient way to develop, package, and deploy applications. However, they do come with their security risks. In this blog post, we have explored the common container vulnerabilities, and what they resulted in for some organizations. We’ve also discussed how to manage these vulnerabilities throughout the application workflow. Devtron provides a centralized platform to integrate industry-leading vulnerability scanning tools seamlessly into your workflow. This allows you to identify and address vulnerabilities early on, ensuring a more secure and robust application pipeline. By leveraging Devtron's capabilities, you can:
- Automate vulnerability scanning across all stages of development and deployment.
- Define security policies to enforce secure deployments.
- Continuously monitor your production environment for vulnerabilities.








