What is Kubernetes container security, and why does it matter? Kubernetes container security involves protecting containerized applications and infrastructure from vulnerabilities during build, deployment, and runtime. As companies adopt CI/CD pipelines to deploy apps in Kubernetes, faster release cycles introduce new security risks. Traditional post-deployment security methods are no longer sufficient. Containers share the same host OS, so compromising one can impact others.
How does DevSecOps improve Kubernetes container security?DevSecOps integrates security early in the development process, shifting left in the CI/CD lifecycle. It ensures security isn’t an afterthought but a built-in part of coding, testing, and deployment.
This guide explains key DevSecOps practices for securing Kubernetes containers, including policies, image handling, runtime protection, and using platforms like Devtron.
Policy and Governance for Kubernetes Application
What are Kubernetes policies and governance in container security? They are a set of security rules and practices to protect microservices and ensure compliance with standards like HIPAA, GDPR, and PCI DSS.
Which Kubernetes policy tools help with governance?
Pod Security Policies (PSP) and Network Policies are built-in frameworks. PSPs define rules for pod creation and management; Network Policies manage inter-pod communication to control traffic flow.
Who enforces policies in a DevSecOps workflow?
DevSecOps teams apply policies throughout the CI/CD process, ensuring security is enforced during development, testing, and deployment.
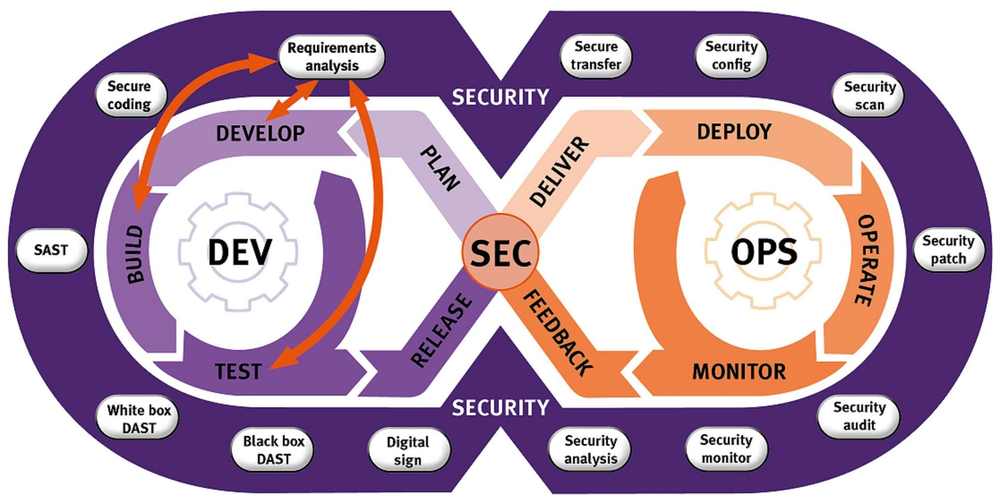
DevSecOps Best Practices for Kubernetes Container Security
What are the best practices for securing Kubernetes containers in DevSecOps?
Below are essential practices categorized by build, deploy, and runtime phases:
Secure your container image creation
- How do you secure base container images? Use updated, patched base images and scan with tools like Docker Scout.
- What is a multistage build, and why use it? Multistage builds reduce container image size by copying only essential binaries, lowering the attack surface.
- Why restrict exposed ports? Only expose required ports to minimize network exposure.
Let’s take a look at an example of multi-stage builds. In the below example, we will be using 2 base images golang:1.15-alpine and alpine:3.12
The first builds the application, and the second runs the application.
# Stage 1: Build
FROM golang:1.15-alpine as builder
WORKDIR /app
COPY go.mod go.sum ./
RUN go mod download
COPY . .
RUN CGO_ENABLED=0 GOOS=linux go build -a -installsuffix cgo -o main .
# Stage 2: Run
FROM alpine:3.12
RUN apk --no-cache add ca-certificates
WORKDIR /root/
COPY --from=builder /app/main .
CMD ["./main"]
Automatically pull container images from registered sources
- What should you check before pulling container images? Ensure images are signed, official, up-to-date, and from trusted registries such as DockerHub.
- How to maintain image security over time? Continuously scan images for security vulnerabilities using Trivy, Clair, or similar tools, and use hardened base images
Ensure container security during the deployment
Why is securing the host OS important?If the host OS is compromised, all containers are at risk. Use a minimal OS and isolate access.
- What techniques help isolate containers? Network segmentation by isolating containers from the host can help ensure that the containers cannot access sensitive data in the host file system
- How do user namespaces help in isolating containers? User Namespaces is a Linux API that helps to isolate specific parts of the OS. Each user namespace acts as a separate container, and they are isolated environments.
- What is Container Sandboxing? Sandbox containers create virtual environments by adding a new runtime that starts a container inside them. Kata containers are a tool that helps in container sandboxing.
- How do SELinux and AppArmor help in securing the container?SELinux and Apparmor integrate in the Linux Kernel to implement policies that limit container access to the host’s filesystem. These can also limit the container actions.
Ensure container runtime security
- What security policies help secure the container runtime? Apply least privilege, run containers as non-root, and restrict runtime API access.
- How does logging help runtime security? Runtime logs detect unauthorized actions and aid in incident investigation.
- How to limit access to the container runtime daemon and APIs?Prevent access to the underlying system that the container runtime is running on using access controls such as authentication and authorization mechanisms.
Enforce Kubernetes environment security
- What tools help secure the Kubernetes environment?Use RBAC for access control, Network Policies for pod isolation, and secret management solutions such as Azure vault or external Secrets help with securing kubernetes environments.
- How to enforce compliance at the API level? Use admission controllers like PSPs and enable audit logging of all API interactions.
- What is the purpose of securing the etcd store in Kubernetes? To protect the etcd data, it’s essential to secure communication between etcd clients and services using firewall rules and TLS encryption.
- What is an admission controller plugin in Kubernetes? Admission Controller checks the incoming request against a set of rules to either allow or deny it, helping govern and enforce policies within the cluster.
These steps ensure security is implemented from image creation to deployment and runtime.
Kubernetes Security Using Devtron Platform
How does Devtron help improve Kubernetes container security?
Securing Kubernetes environments requires consistent enforcement of security policies across the CI/CD pipeline. Devtron, an open-source Kubernetes-native CD platform, addresses challenges across three core areas: authorization, security scanning, and policy enforcement.
Why use Devtron for Kubernetes CI/CD security?
DevSecOps teams often struggle with integrating multiple security tools. Devtron simplifies this by offering a native CI/CD platform that embeds security features directly into deployment workflows.
How does Devtron manage authorization and access control?
Devtron enables teams to configure SSO, role-based access control (RBAC), permission groups, and API tokens to manage access across users, services, and Kubernetes resources.
How does Devtron handle vulnerability scanning?
It integrates tools like Trivy and SonarQube into its pipelines. Vulnerabilities are detected during the image build stage. When critical issues are found, deployments are halted automatically.
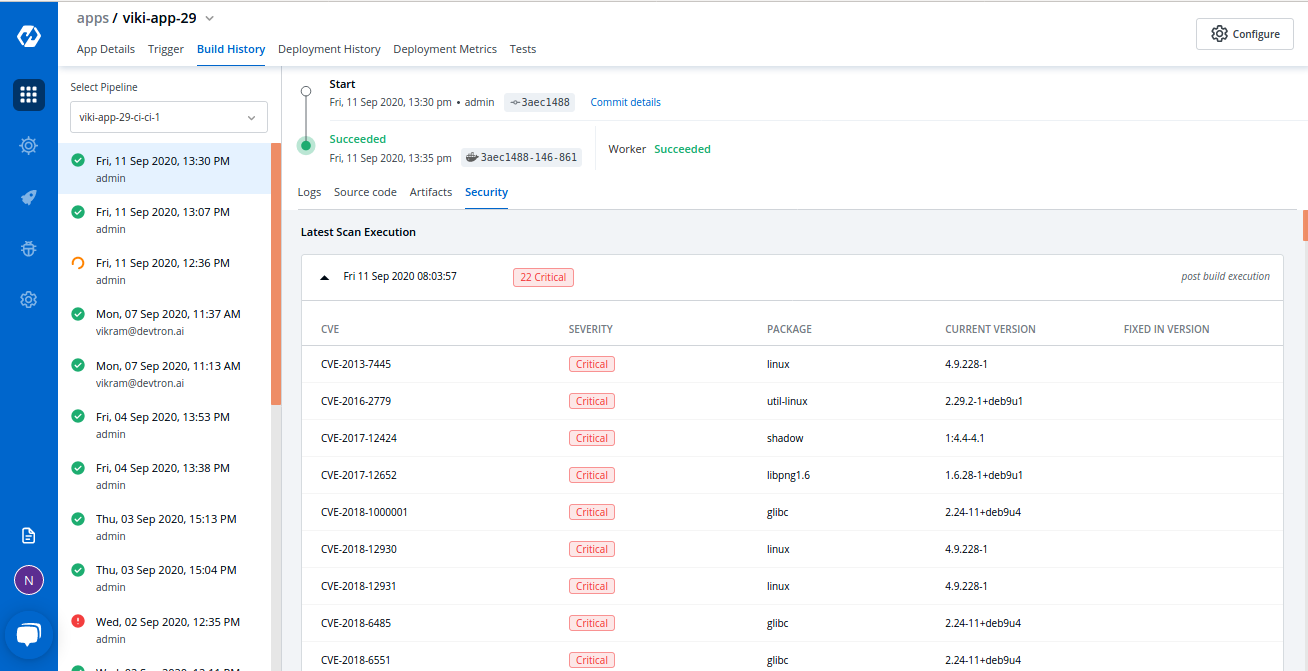
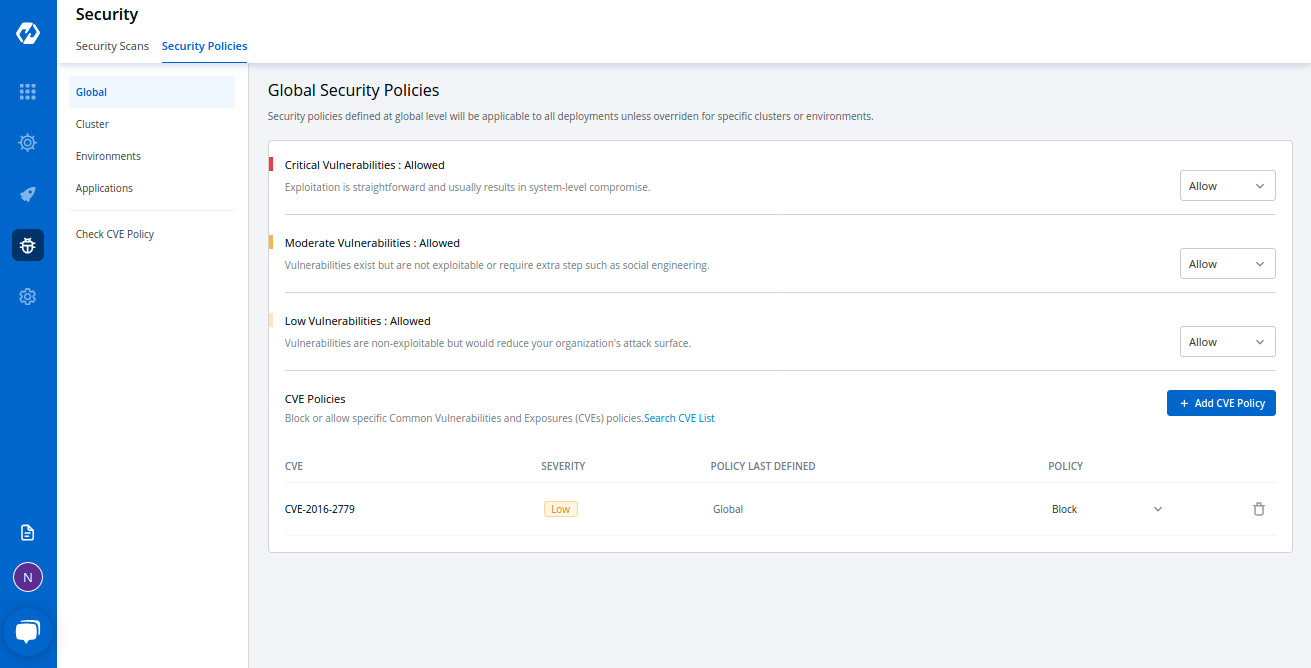
Can I enforce custom security policies in Devtron?
Yes. You can define security rules based on severity (e.g., critical, moderate, low) and enforce policies like blackout windows or environment-based restrictions. These can be applied globally or at the cluster, user, or application levels.
Devtron allows you to scale DevSecOps practices with native policy control, automated scanning, and integrated access management.
Commonly Asked Questions
How do you secure Kubernetes containers using DevSecOps?
You secure Kubernetes containers by embedding DevSecOps best practices across the CI/CD pipeline. This includes scanning container images, isolating workloads from the host OS, running containers as non-root users, using RBAC and network policies, and enabling admission controllers like Pod Security Policies. These steps reduce the attack surface and maintain compliance from build to runtime.
What are the biggest security risks in Kubernetes containers?
Containers can share a host OS, exposing all to risk if one is compromised. Other risks include unscanned base images, misconfigured RBAC, or insecure Secrets.
How is DevSecOps different from traditional DevOps in Kubernetes?
DevSecOps integrates security from the start of development—scanning images, enforcing policies, and automating compliance inside CI/CD pipelines
What tools can I use to scan container images for vulnerabilities?
Tools like Trivy, Clair, and SonarQube are commonly used to identify CVEs and other security flaws in Docker images during build time.
How does RBAC improve Kubernetes container security?
Role-Based Access Control (RBAC) limits who can access or modify Kubernetes resources, reducing the risk of unauthorized changes or privilege escalation.
Can Devtron help enforce Kubernetes security policies?
Yes. Devtron allows you to set global and environment-specific security rules, perform vulnerability scans, and restrict deployments based on policy violation







