Organizations seek ways to optimize resources and reduce operational costs in the fast-paced cloud-native landscape. Kubernetes has become the go-to platform for the orchestration of containers, providing easy scaling and efficient ways to manage applications. One powerful feature of Kubernetes is multi-tenancy.
Multi-tenancy in Kubernetes enables organizations to share cluster resources among multiple teams or applications, reducing costs and enhancing efficiency. Let's discover how Devtron simplifies multi-tenant Kubernetes management, offering scalable and secure operations.
Multi-tenancy
Multi-tenancy in Kubernetes refers to the ability to share the resources of a Kubernetes cluster among workloads, individuals, teams, or even different organizations. At the same time, you also need to ensure secure isolation and controlled resource allocation by each tenant.
To understand the concept of multi-tenancy imagine: you are in an organization with multiple teams. Each team requires a Kubernetes cluster, and spinning a separate cluster for each can become inefficient and costly. So what you will be doing is, you will spin a single Kubernetes cluster and onboard all your teams as tenants in a single shared cluster. Where your teams can deploy their workloads securely and isolatedly, you can use Namespaces, Resource Quotas, and Network Policies to achieve isolation. Following this approach you will optimize resource utilization, reduce infrastructure costs, and simplify the management of clusters.
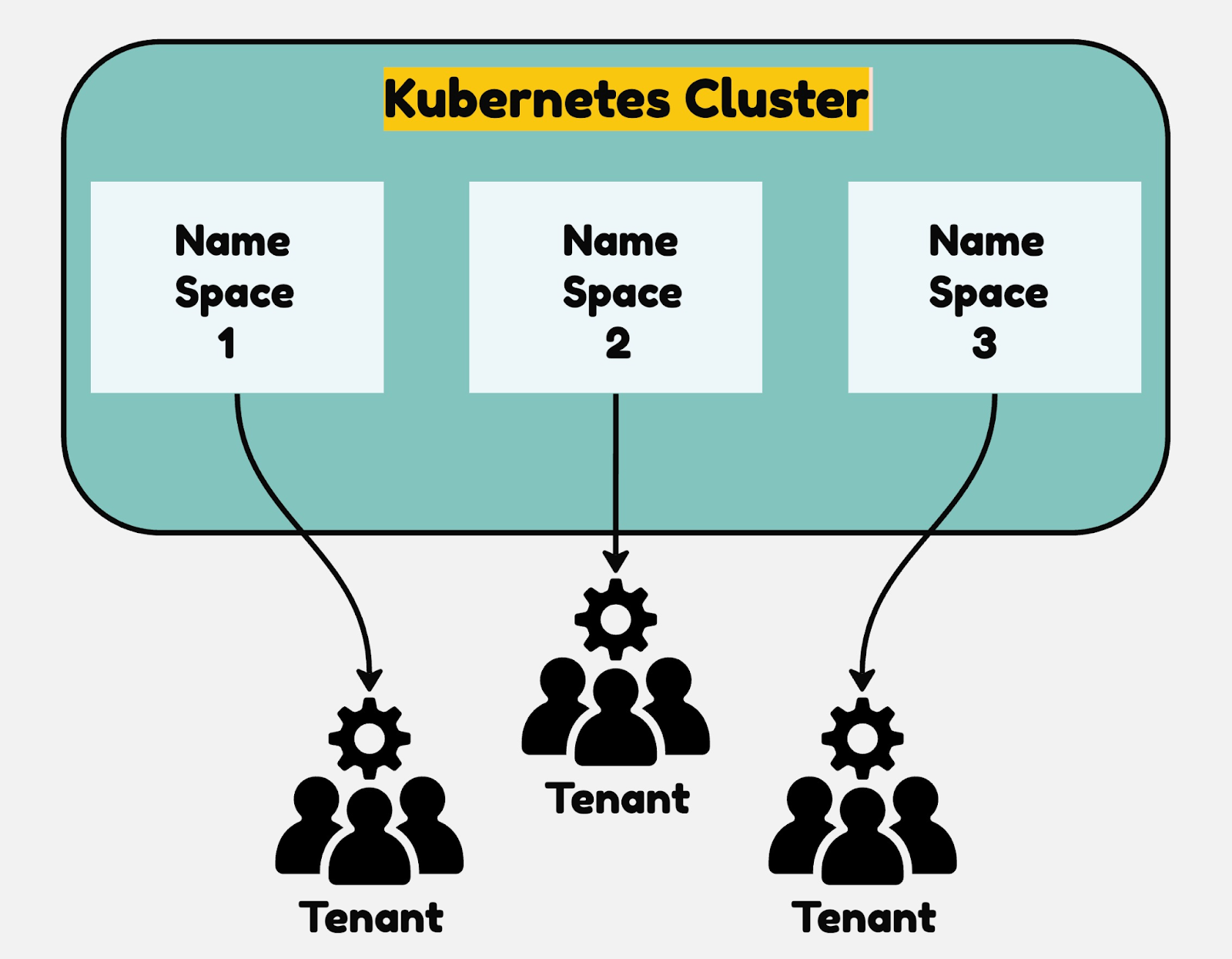
The use case of Multi-tenancy falls into two categories.
- Multiple teams: Here, a shared cluster is being used by teams from the same organization.
- Multiple Customers: When a SaaS vendor spins a shared cluster. And, customers are using it.
Simplify Multi-Tenant Kubernetes Administration with Devtron
- Effortless Creation of Tenant Environments: Simply create different environments for different tenants within the same or different clusters with secure and optimized usage of resources.
- Centralized Release Tracking: Monitor and control releases across multiple tenants from a single dashboard, streamlining software distribution and enhancing operational efficiency.
- Enhanced Security with SSO and RBAC: Implement Single Sign-On (SSO) and fine-grained Role-Based Access Control (RBAC) for secure authentication and authorization processes within tenant environments.
Experience smooth multi-tenant Kubernetes operations with Devtron.
Components of Multi-tenancy
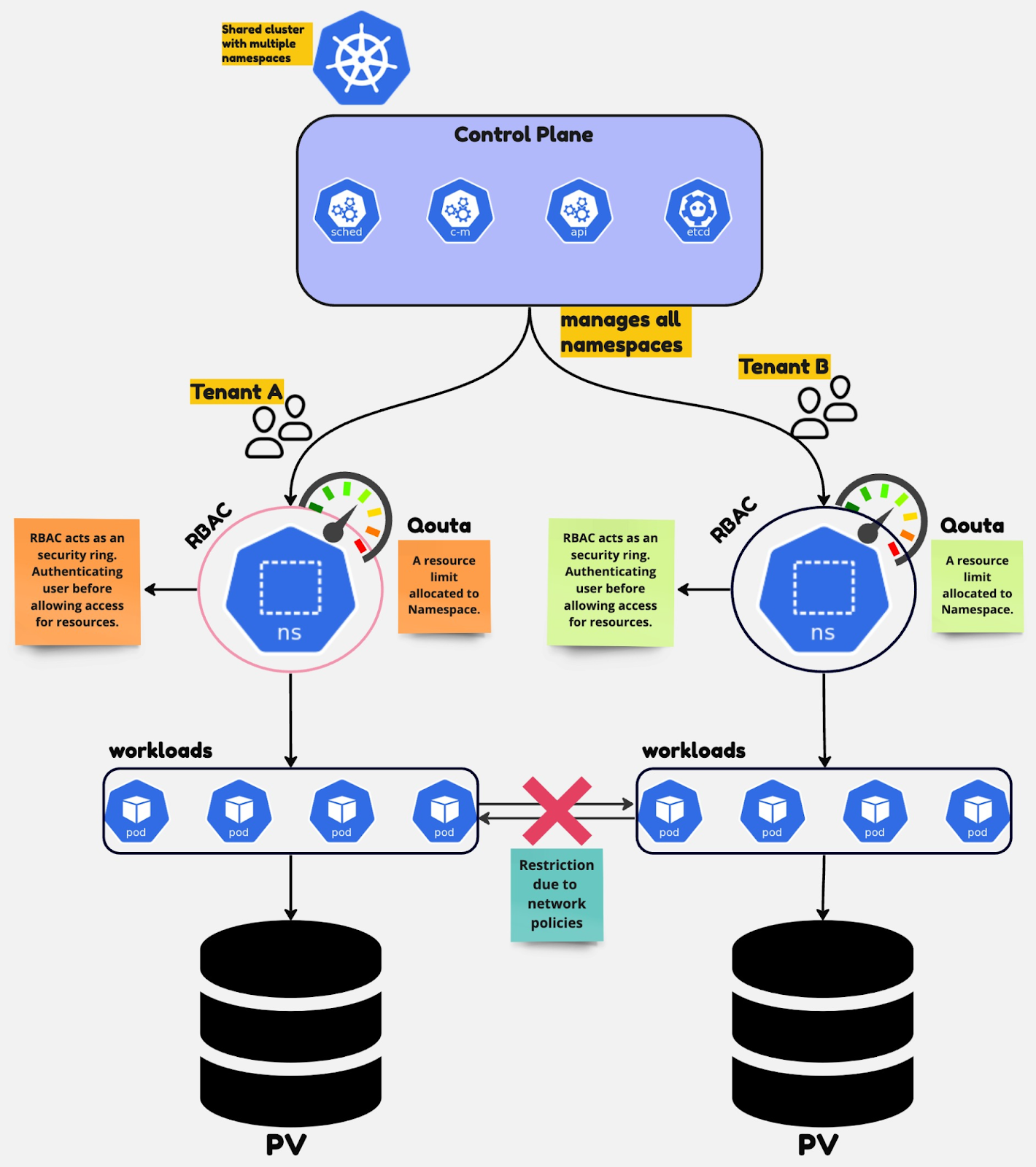
Teams and customers using shared clusters care about security and isolation. Kubernetes provides components to achieve security and isolation. These components include Namespaces, Resource Quotas and limits, Storage, Network Policies, and Access Control, like role-based access control (RBAC).
Control Plane Isolation
Kubernetes offers objects like Namespaces, Quotas, and RBAC to achieve control plane isolation.
Namespaces are the fundamental component of Kubernetes. This component plays a crucial role in multi-tenancy. With Namespace, you can logically partition a single Kubernetes cluster into multiple virtual clusters, each with its resources and policies. In the context of multi-tenancy, namespace creates virtual boundaries that isolate the tenant's workload. Each tenant can be assigned a separate namespace, ensuring that their resources are separated from others.
Other components, like Quota and RBAC, are within the scope of the namespace.
RBAC is used for authorization purposes in the Kubernetes control plane. The RBAC is for both users and workloads. Using RBAC, isolated access to Kubernetes resources can be achieved by setting appropriate RBAC rules.
The Quota in Kubernetes refers to the resource limit allocated to each namespace. As a restriction, Kubernetes also asks the user to specify the resource required by the container in that namespace. This component ensures tenants cannot consume more cluster resources than allocated. Reducing the issue of noisy neighbors.
Data Plane Isolation
You can achieve data plane isolation by configuring storage isolation and Network Policies.
In Kubernetes, all pods can communicate with each other, but the unencrypted network traffic can lead to security threats. The Network Policies in multi-tenant Kubernetes clusters are rules. They restrict communication between pods. The restrictions are based on the pod’s namespace and IP range. When working with shared clusters, use strict Network Policies. Kubernetes provides a default one to start with. That allows for keeping the data traffic of tenants separate and secure.
Kubernetes provides multiple storage options for workloads that can be used as persistent storage options, ensuring storage isolation. For the shared Kubernetes cluster where every tenant requires isolation, we can use persistent volume claims (PVC). These are the namespace resources that allow the pods to request persistent storage. When a pod requests storage using a PVC, Kubernetes dynamically provisions a PersistentVolume (PV) based on the storage class.
To understand these parts better, imagine you are a DevOps engineer. Your task is to set up a shared Kubernetes cluster. An internal team of developers will use the cluster to test their applications. To ensure proper isolation in the shared cluster you will be defining dedicated Namespaces for each member.
As we know that the RBAC and Quota are scoped to the namespace, you will define the resource limit, which is the resource Quota, for each namespace.
You will set RBAC rules to authorize access. They will restrict team members from accessing another namespace allocated to someone. If you want to restrict the internamespace communication you will be defining the Network Policies at the Data Plane level. You can isolate the storage for each team member with the use of StrorageClass and PersistentVolumeClaims. You can use these components together. They let you set up a secure shared cluster for developers. They can deploy their apps without impacting each other.
Multi-tenancy Strategies
There are two major strategies to implement multi-tenancy in your Kubernetes cluster.
Soft Multi-tenancy
- You cannot provide strict isolation between tenants and their workloads.
- It’s suitable for trusted tenants from the same organization who have no intention to harm each other's systems.
- In Soft multi-tenancy, the focus is on preventing accidental issues through isolation.
- It is implemented using Kubernetes Namespaces.
Hard Multi-tenancy
- It’s implemented where the need for isolation is strict between tenants and their resources.
- It’s suitable for untrusted tenants like tenants from multiple organizations, and multiple customers of SaaS companies.
- The focus is to prevent malicious behavior from other tenants.
- Defining strict policies, Namespaces, or virtual clusters can implement this.
Benefits and Challenges
Benefits
- Improved Operational Efficiency: Using a single cluster reduces operational tasks like updates and security patches, and managing the cluster becomes streamlined.
- Better Resource Utilization: In a shared Kubernetes cluster the resources are dynamically allocated to tenants according to needs. This leads to higher utilization and prevents underutilization and overprovisioning of resources.
- Governance: You get centralized control over policies, such as security, networking, and resource management, ensuring consistent enforcement across all tenants, and enhancing governance and compliance.
- Scalability: multi-tenancy enables organizations to scale their infrastructure more efficiently by adding or removing tenants on-demand, without provisioning or de-provisioning the entire cluster.
Challenges
- Proper isolation and preventing security breaches between tenant workloads.
- Configuration and management of complex policies (Network, RBAC, Resource Quotas) at scale.
- Monitoring and troubleshooting challenges with multiple tenants sharing resources.
- To achieve a fair and equitable resource allocation among tenants.
- Maintaining compliance and meeting regulatory requirements in a multi-tenant environment is necessary.
- Implementation of robust storage isolation and data lifecycle management for each tenant.
Managing Multi-Tenant Kubernetes Cluster
Using a multi-tenant Kubernetes cluster has many benefits. But it also adds complexity. Isolating tenants in multi-tenant Kubernetes clusters needs precise Role-Based Access Control (RBAC). It needs smooth Authentication and Authorization to access resources. It also needs precise Network Policies. Doing all this using kubectl or the Kubernetes API can be hard and error-prone. However, with the right tool, you can mitigate the complexities and eliminate error-prone methods.
Introducing Devtron, a platform designed to eradicate the complexities and provide an easy way to manage your Kubernetes environment. Let’s delve into Devtron and explore what it has to offer when it comes to managing your multi-tenant Kubernetes clusters.
Authentication and Authorization of Tenant
The first step in managing your multi-tenant cluster is the Authentication and Authorization of the tenant. You need to verify the tenant and check for permissions before accessing the resource. For the authentication of the tenant, Devtron provides a Single Sign-On (SSO) feature. Allowing the tenants to easily access the cluster by utilizing their existing credentials.
Once the tenant is authenticated, using the Dashboard of Devtron, you can leverage the robust and precise RBAC for your Kubernetes cluster. Devtron allows you to manage fine-grained access control down to the Kubernetes cluster resource level. You can grant users precise permissions for specific resources in the cluster. The precise, granular access control helps maintain strict isolation between the tenants and their workloads. The Devtron dashboard provides a user-friendly interface for configuring and managing RBAC policies, simplifying granting and revoking permissions.
Managing Resources
Managing a multi-tenant Kubernetes cluster can be complex, as it requires continuous monitoring of resources utilized by tenants, ensuring isolation, and preventing the "noisy neighbor" problem. Additionally, debugging issues for individual tenants becomes challenging, and onboarding new tenants through CLI can be error-prone and lead to granting excessive permissions.
The Resource Browser in Devtron offers a comprehensive suite of features for managing and monitoring multi-tenant Kubernetes clusters. In addition to providing a centralized view of your clusters and enabling easy switching between them, it streamlines the process of setting resource quotas and network policies at the namespace level, ensuring fair resource allocation and isolation between different tenants.
One of the key advantages of the Resource Browser is its built-in debugging capabilities. It allows you to access real-time logs for individual pods, enabling efficient troubleshooting and root-cause analysis. Moreover, these logs can be conveniently exported, facilitating further analysis or archiving for future reference.
The Resource Browser also simplifies the onboarding process for new tenants. Instead of relying on command-line interfaces (CLI), you can leverage the user-friendly interface to create new namespaces for tenants within your multi-tenant cluster. This feature empowers you to provision resources for new tenants quickly and efficiently, without the need for complex CLI commands.
Read more about Resource Browser
Conclusion
Using multi-tenancy can bring many benefits to organizations. These include better resource use, lower costs, improved governance, and scalability. It brings a new set of challenges. These include proper isolation. They also include complex policy setup, monitoring, and troubleshooting for many tenants. An organization can use Kubernetes features to do this. They can use namespaces, resource quotas, network policies, and RBAC. This allows them to enable multi-tenancy for trusted teams or strict policies. It adopts soft multi-tenancy for trusted data. It uses hard multi-tenancy for strict policies. Multi-tenancy in Kubernetes offers a powerful solution. It optimizes resources, cuts costs, and fosters agility. So, it's invaluable in the ever-evolving cloud-native landscape. Managing the multi-tenant Kubernetes cluster is complex in itself, and when we try to manage it using a traditional tool like kubectl it can be error-prone too. Devtron comes with specially crafted features for Kubernetes. The SSO and precise RBAC provided by Devtron make the authentication and authorization process smooth. The Resource Browser of Devtron comes with many features like creating new resources, setting network policies, and editing live manifests for debugging that can help manage Kubernetes clusters.
If you have any queries, don't hesitate to connect with us. Join the lively discussions and shared knowledge in our actively growing Discord Community.